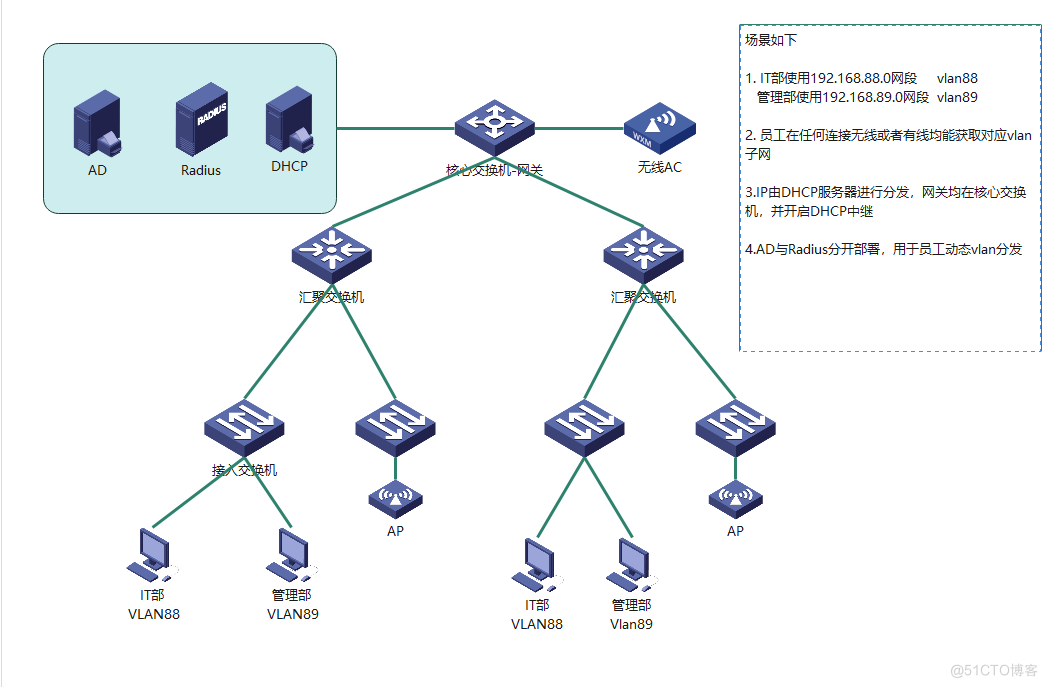
在企业中,不同部门之间采用VLAN进行隔离,但是随着人员流动,部门人员不集中,网络管理难度加大,导致网络权限划分复杂。故引入动态vlan与AD域用户,员工登录无论在哪里登录,都在部门vlan中,获取的IP不变,下面介绍具体实现步骤
实验拓扑如下
以下配置较为简单,故此处不展开
包括:DHCP服务器配置、主干链路vlan接口类型配置
设备如下:
域控可与Radius为同一台windows server
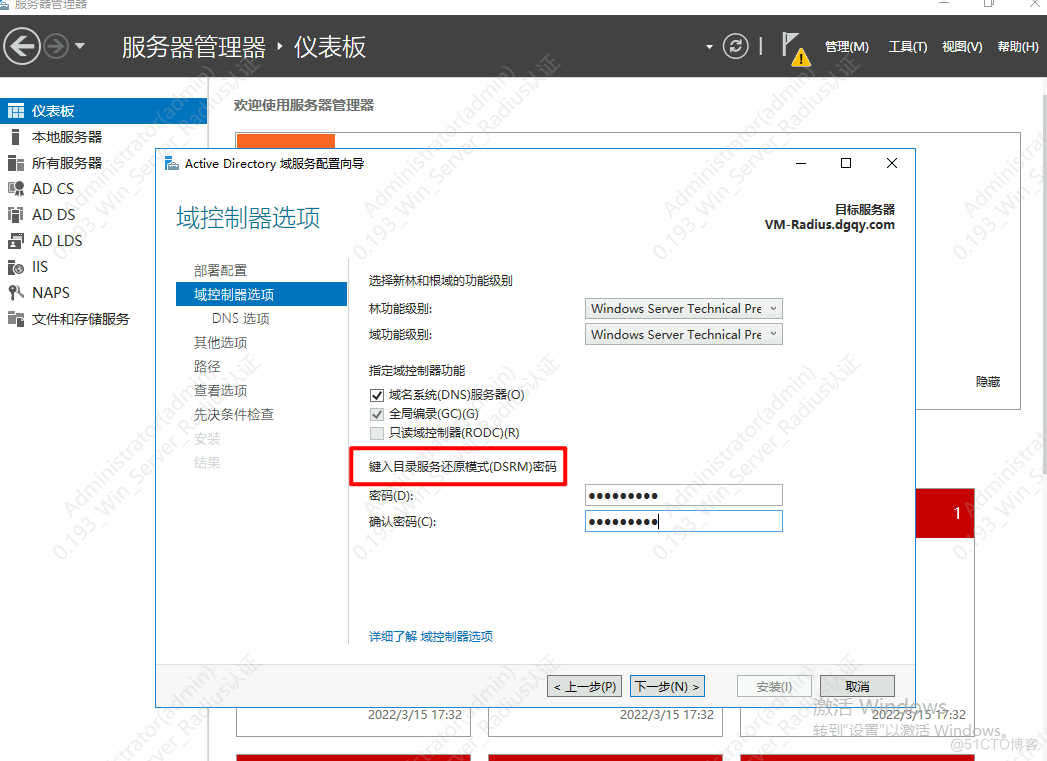
AD域控 (Windows Server )Raidus 服务器 (Windwos Server2016)H3C交换机(S5024为例)(可选)信锐AC+AP二、AD域控用户管理1.AD域安装(已有此环境请忽略)

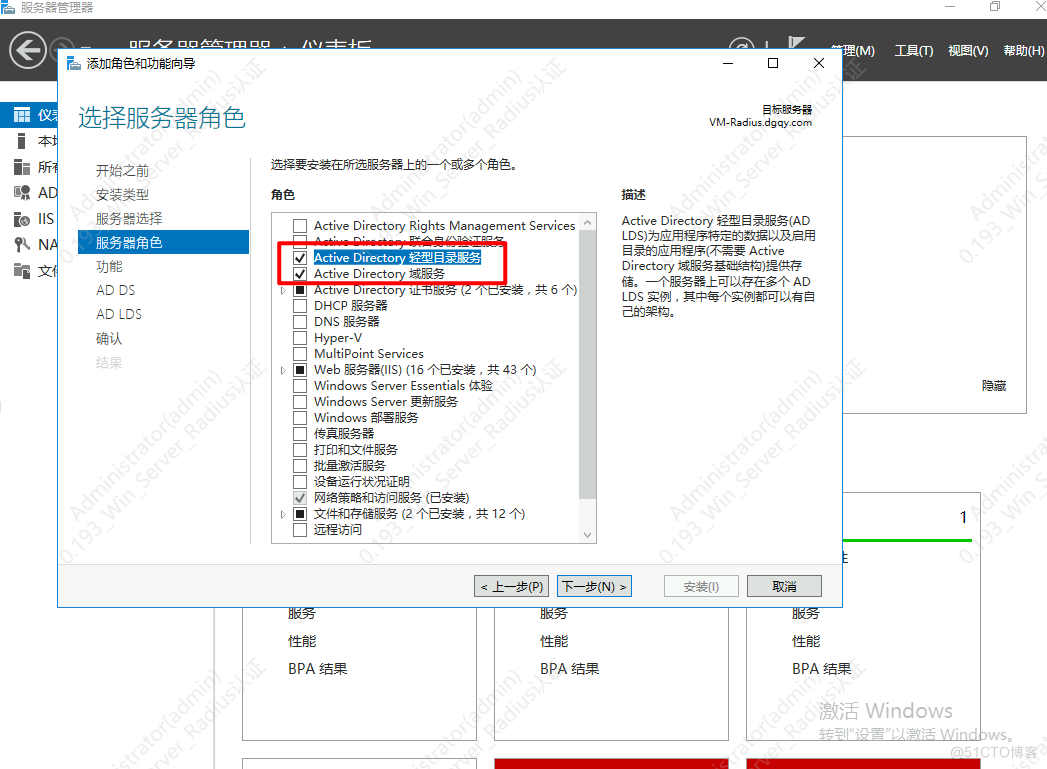
一直下一步

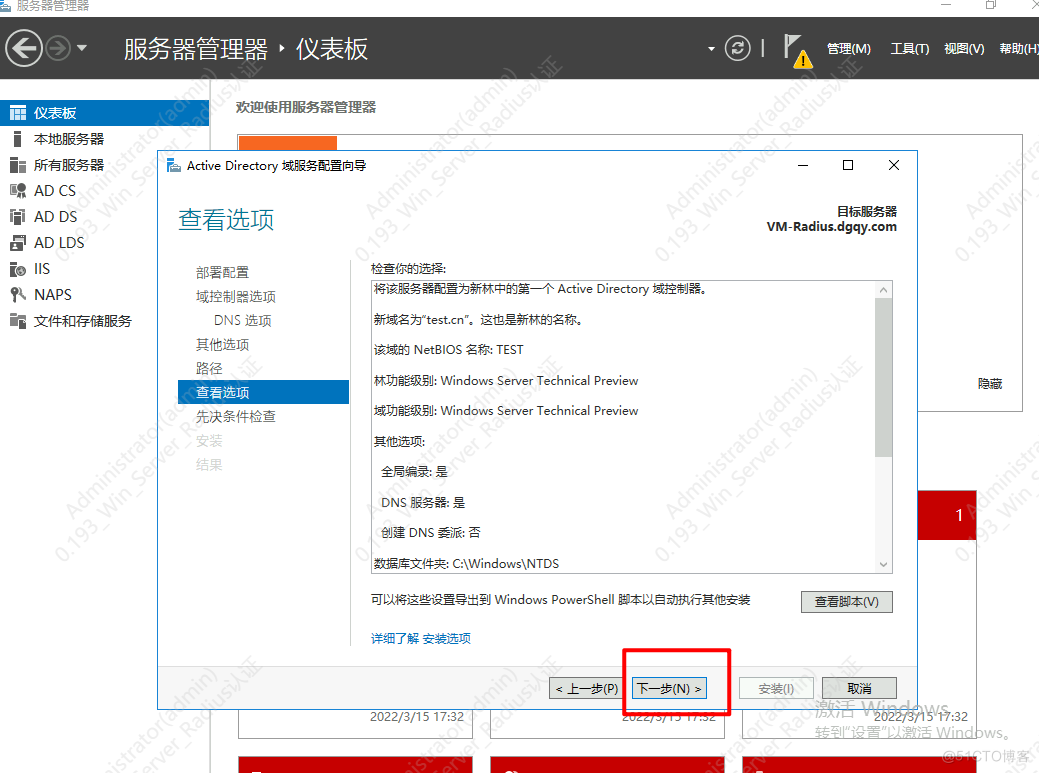

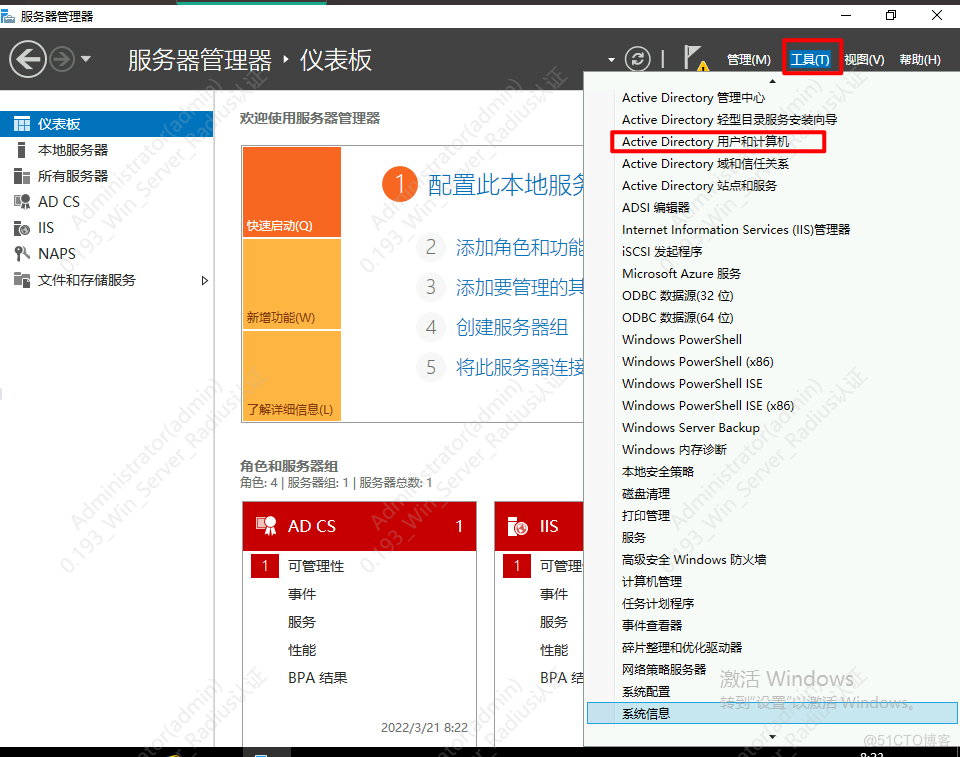
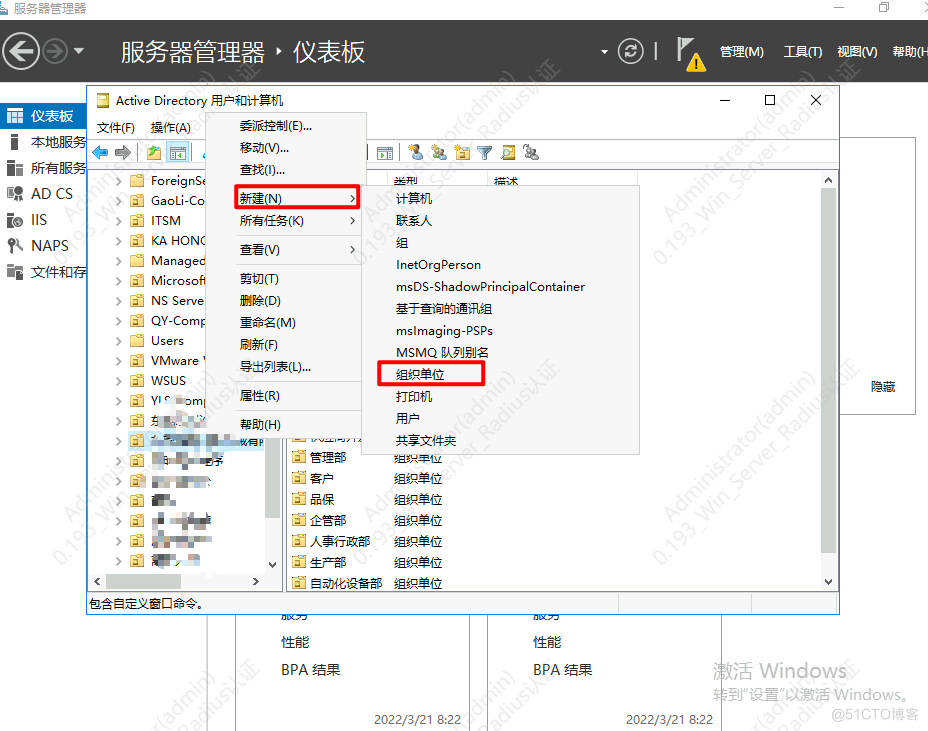
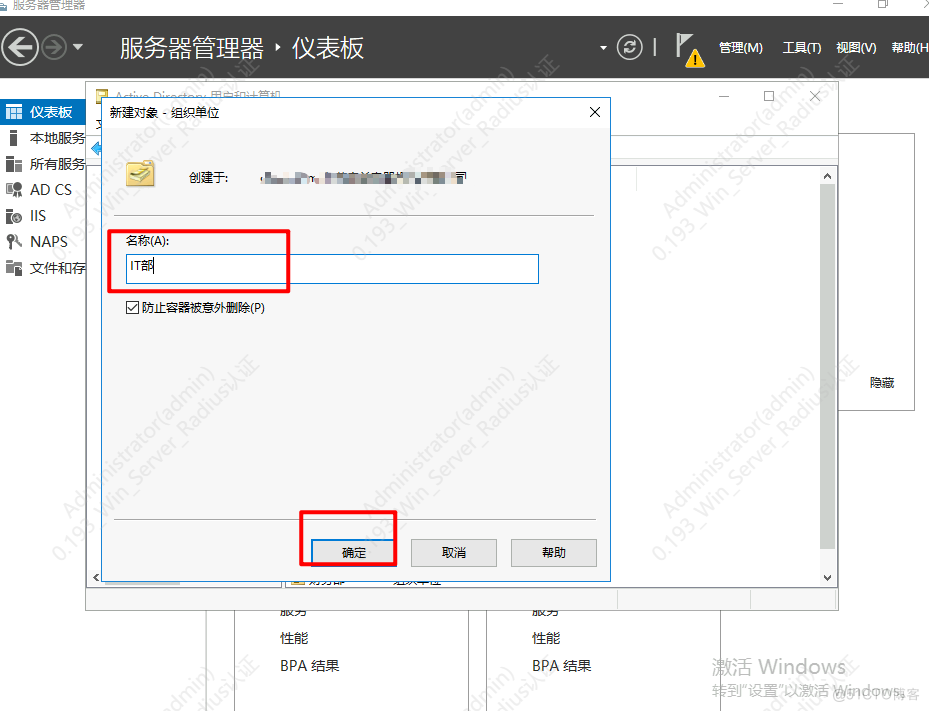
创建OU
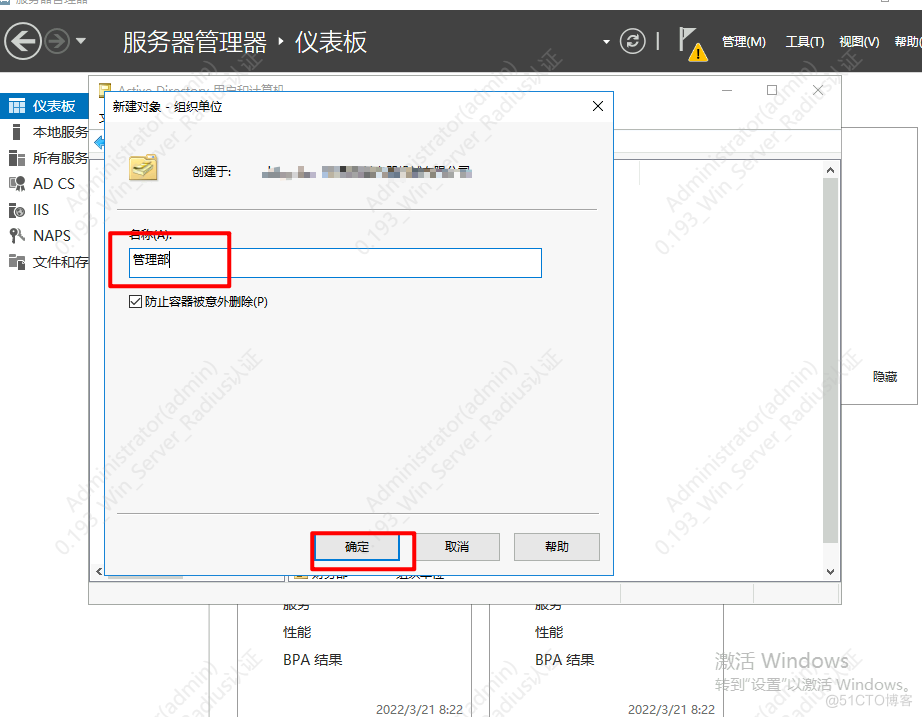
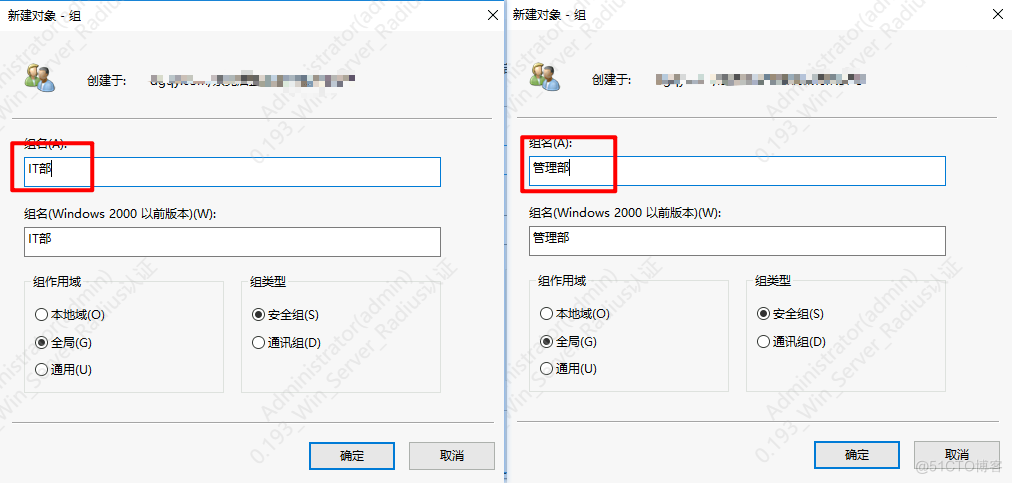
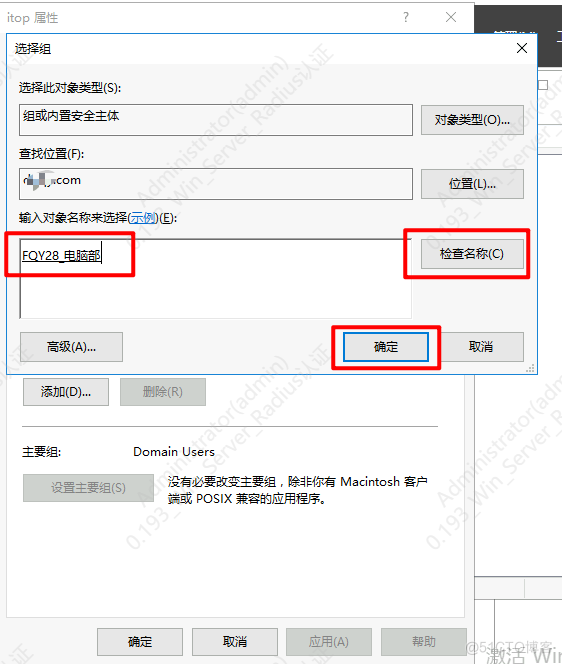
创建组
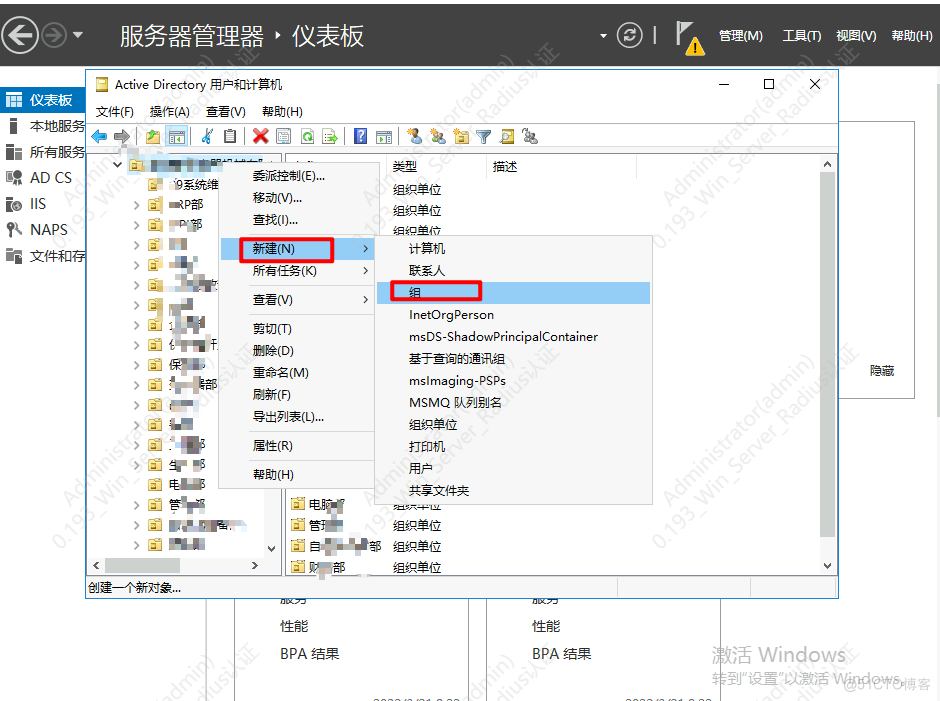
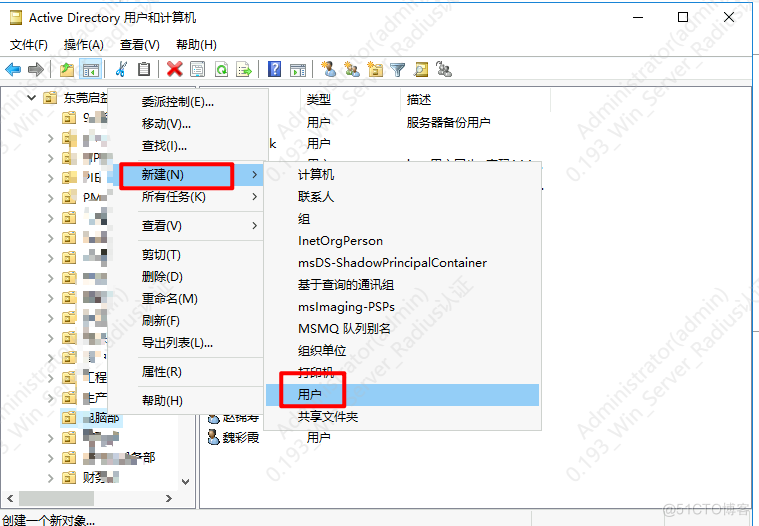
创建用户
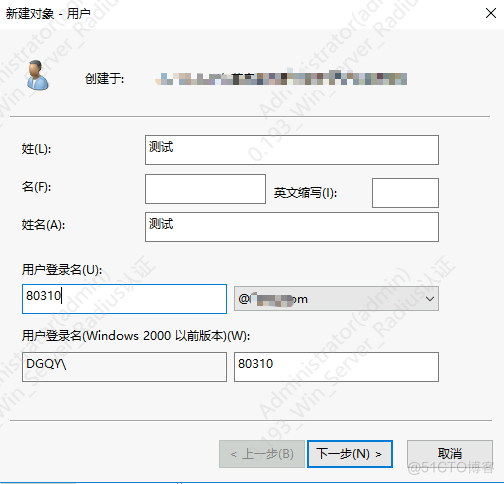
添加到对应组

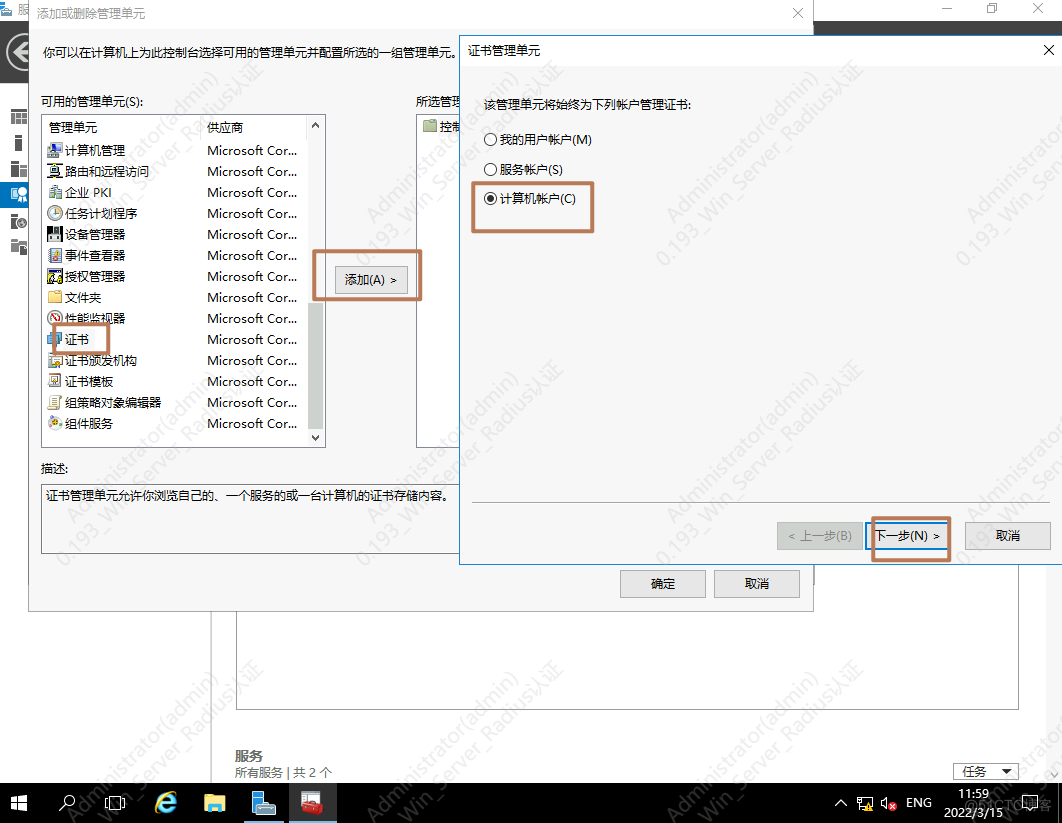
前提:该服务器加入AD域
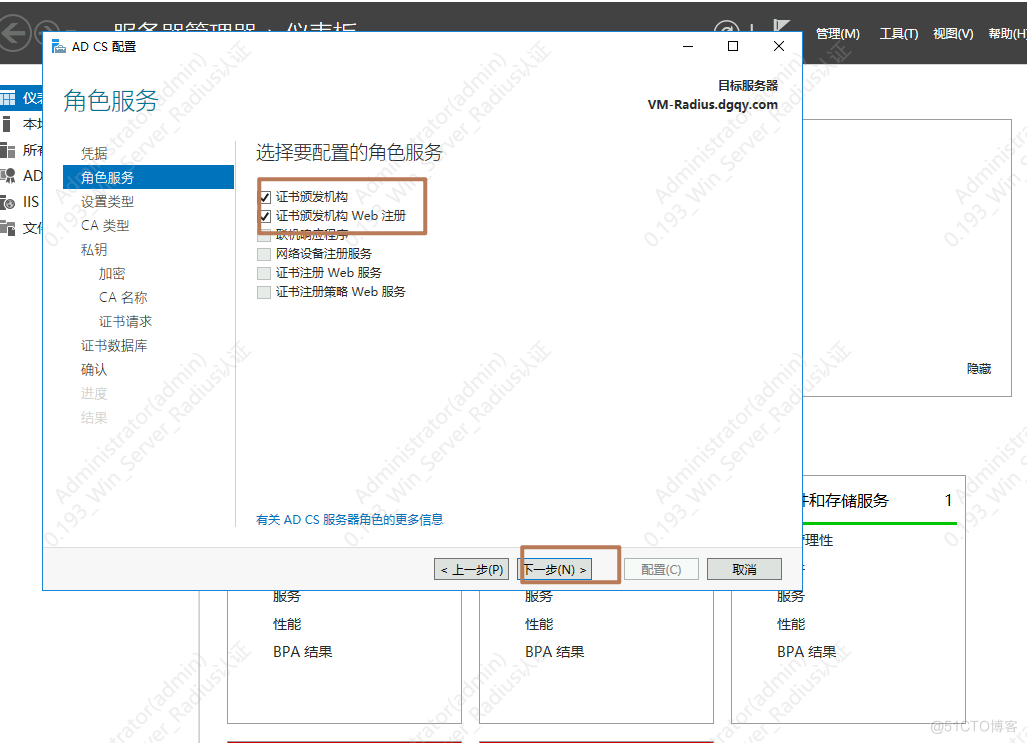
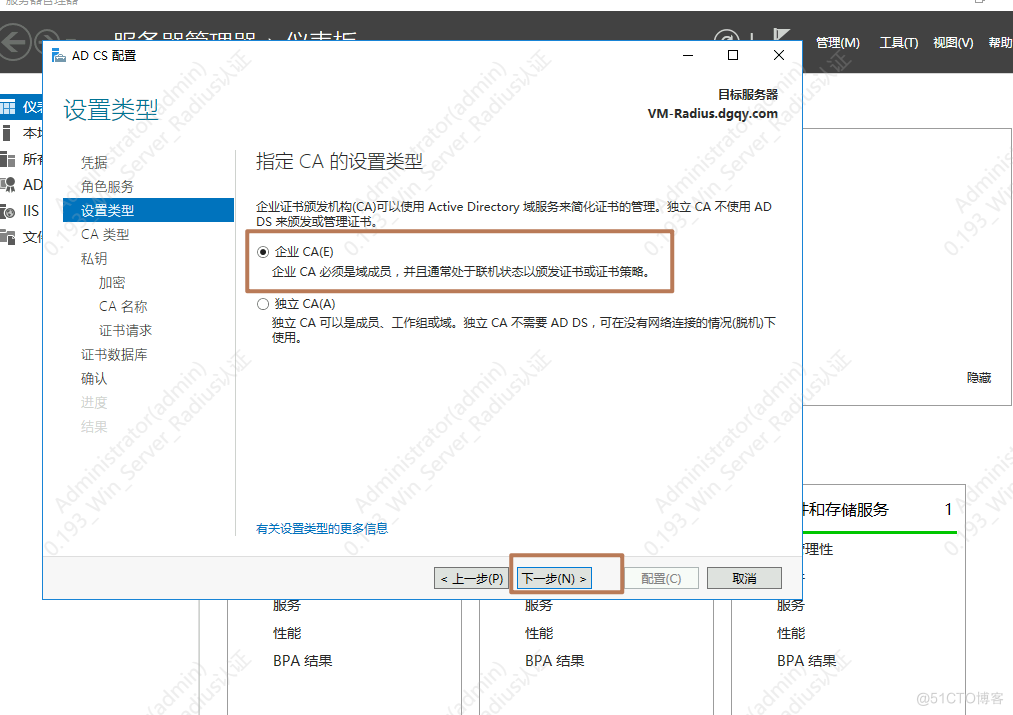
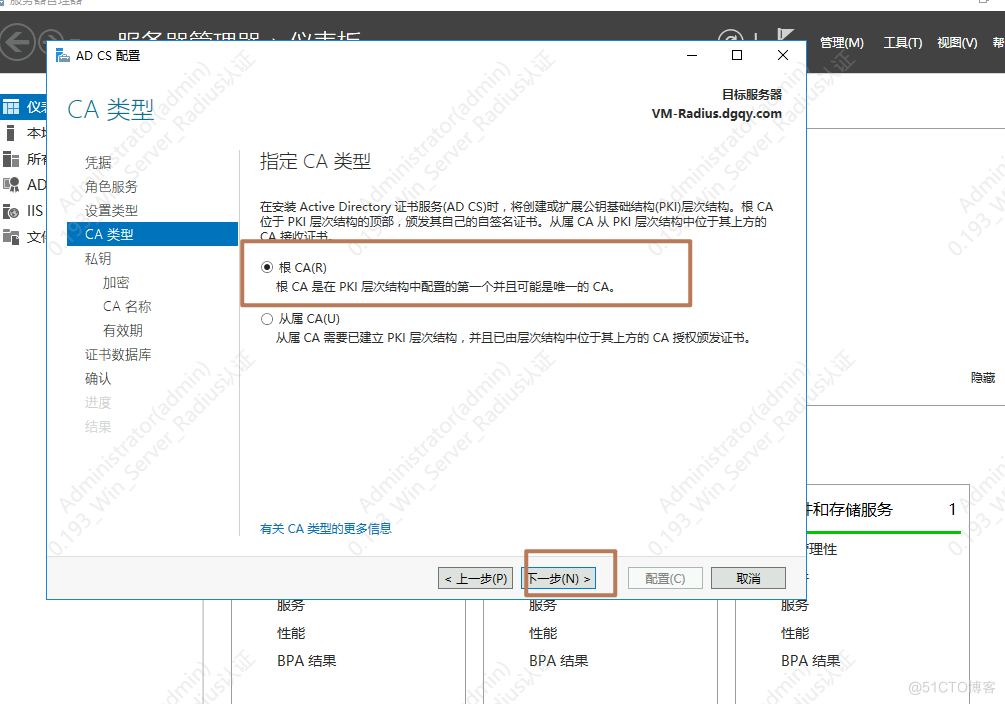
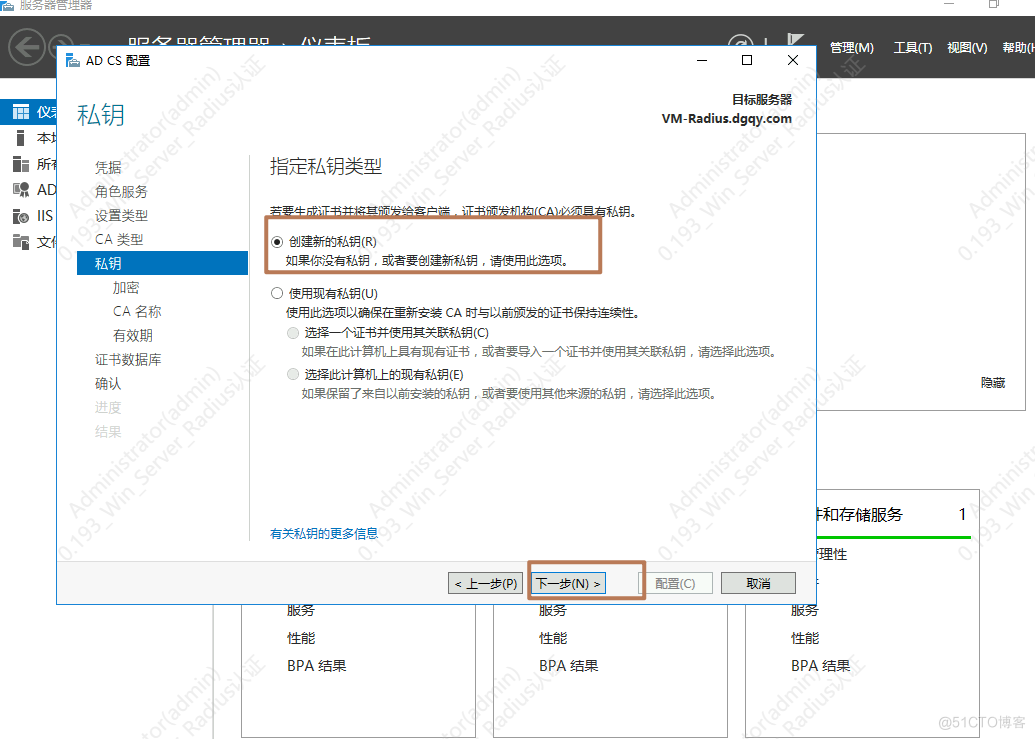
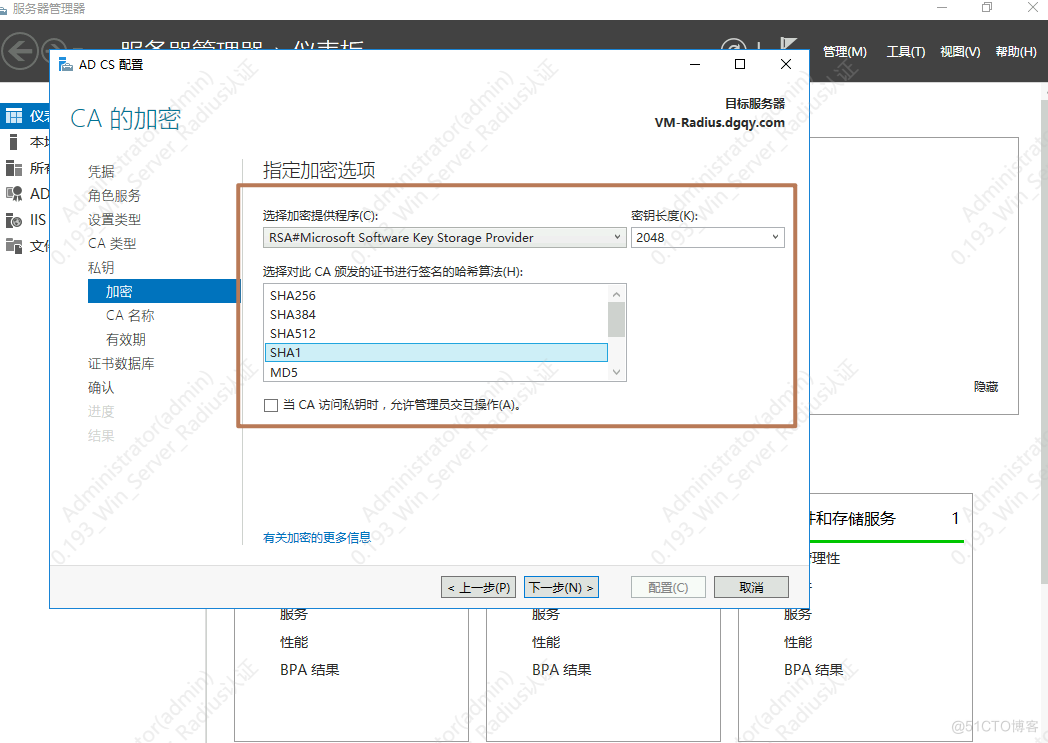
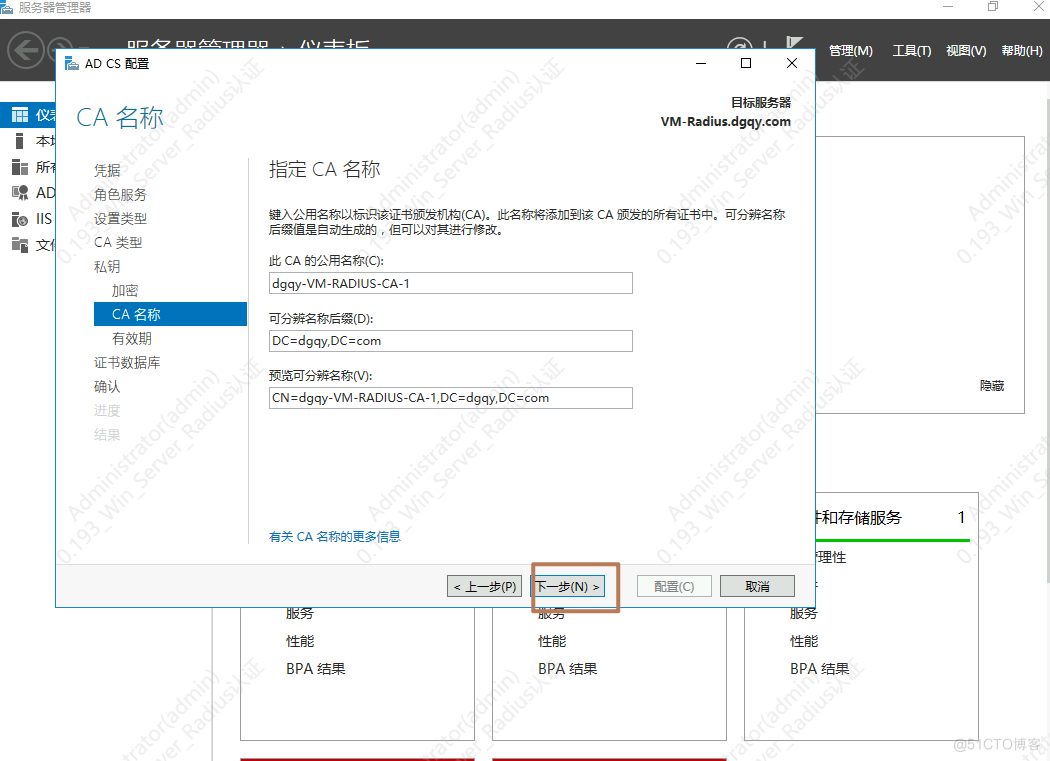
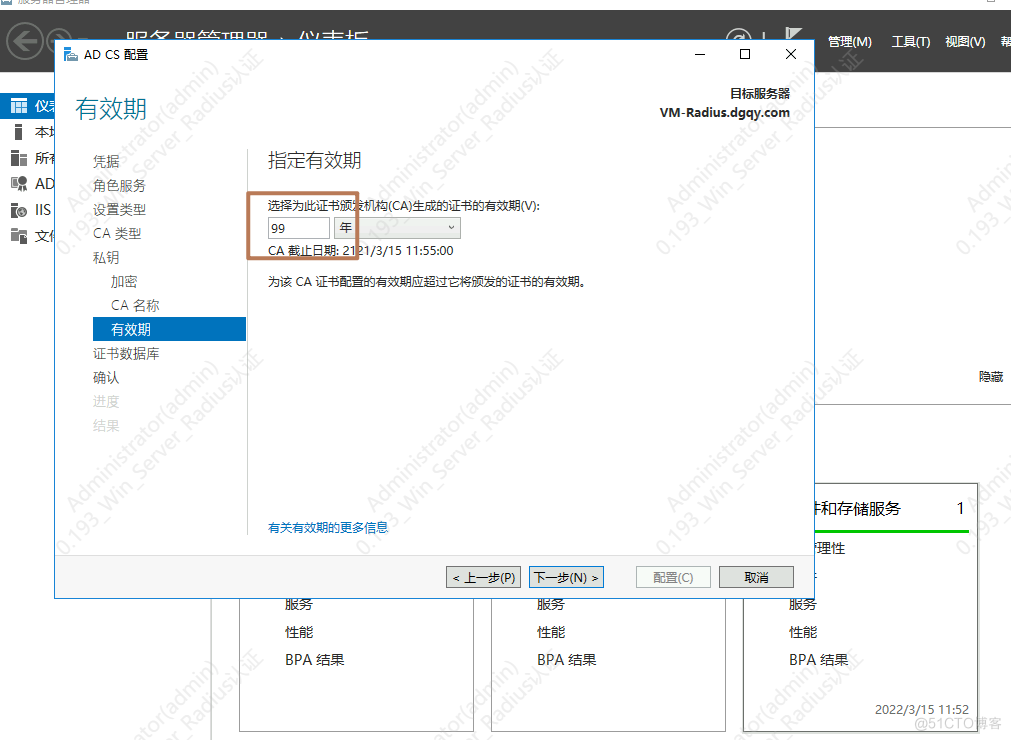
1.安装AD证书
一直下一步
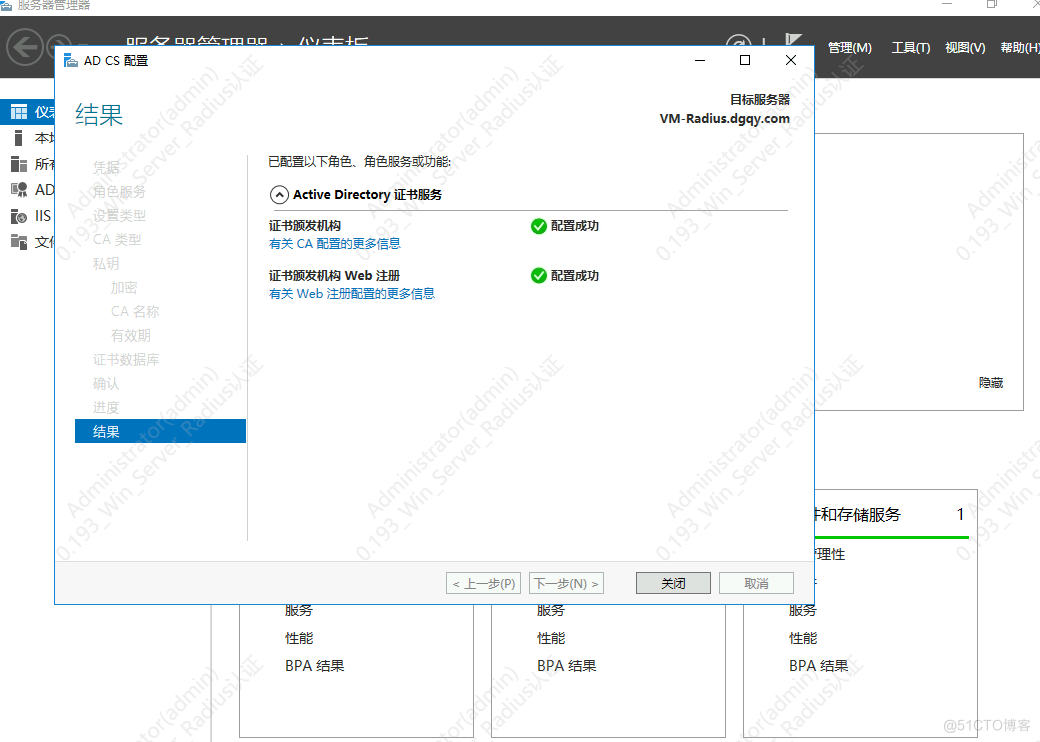
等待安装完成
装完成



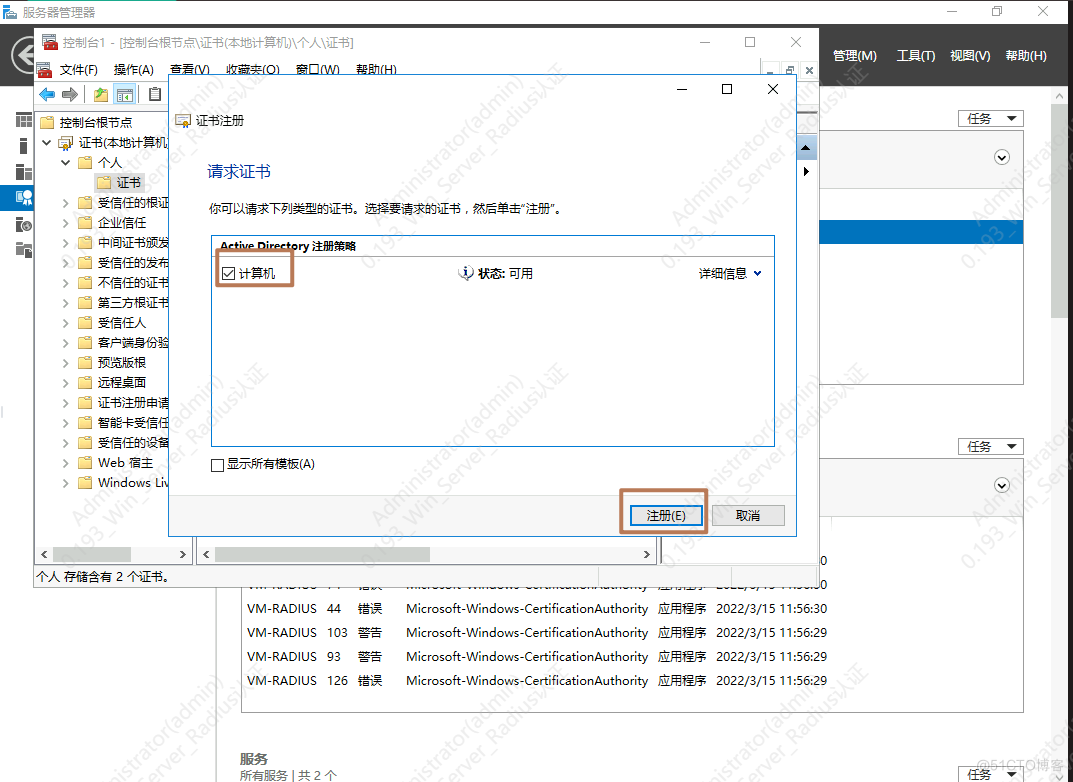
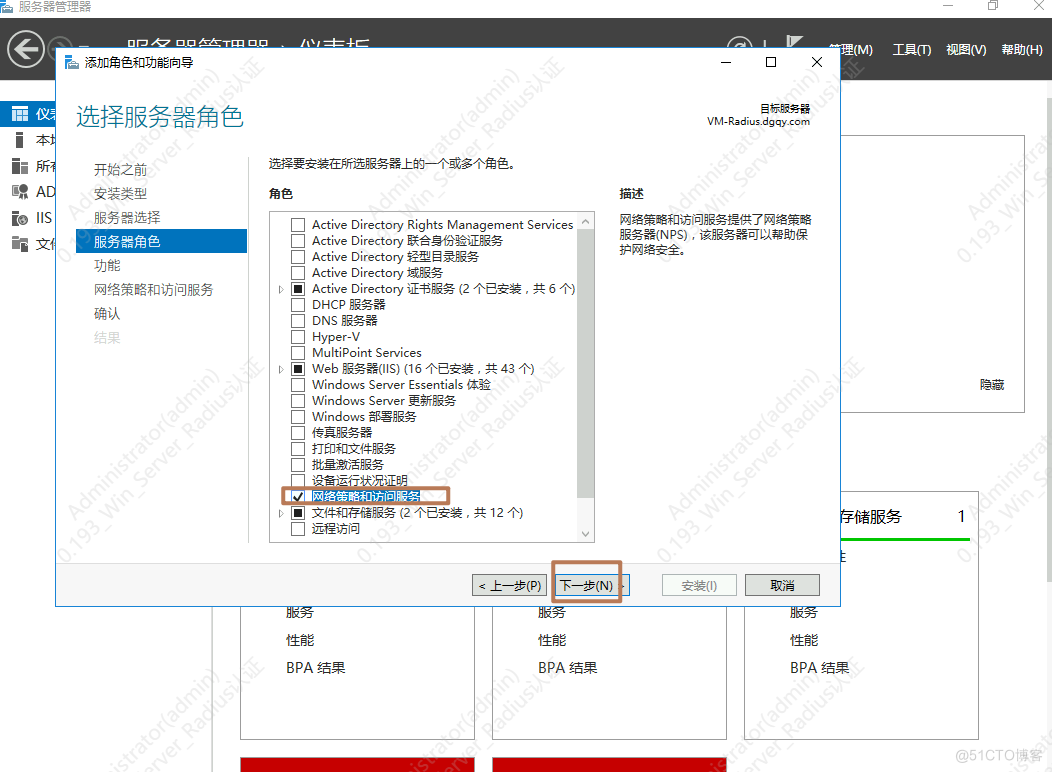

1.配置802.1x策略

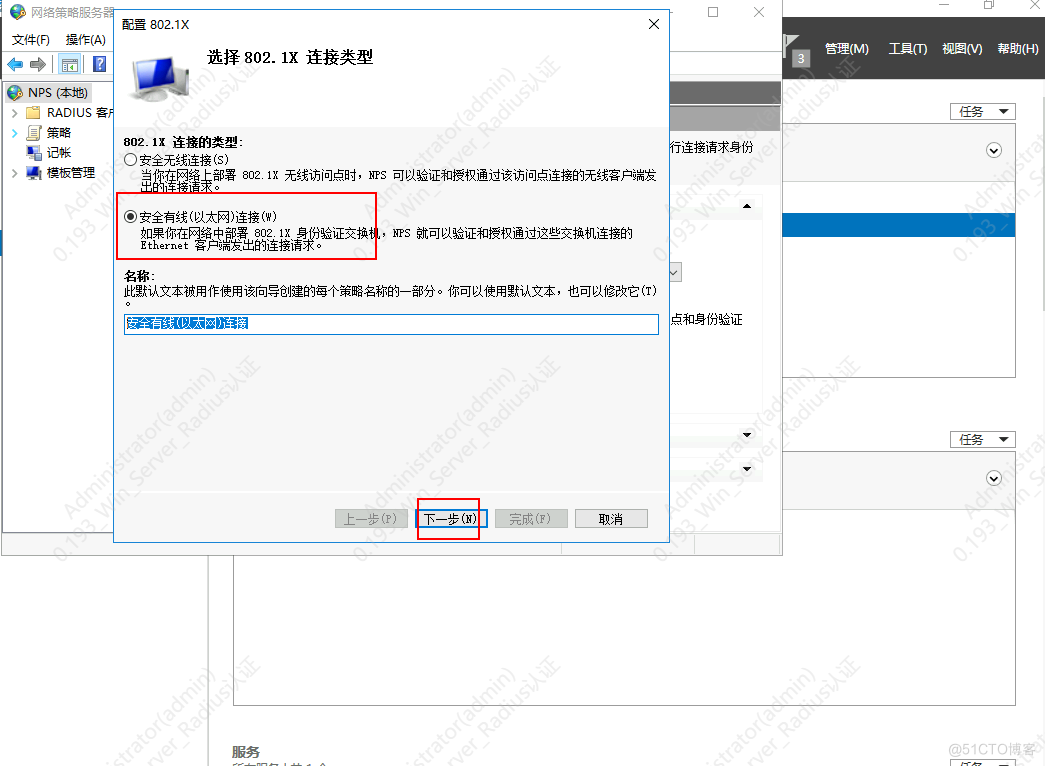
2.配置客户端IP与秘钥
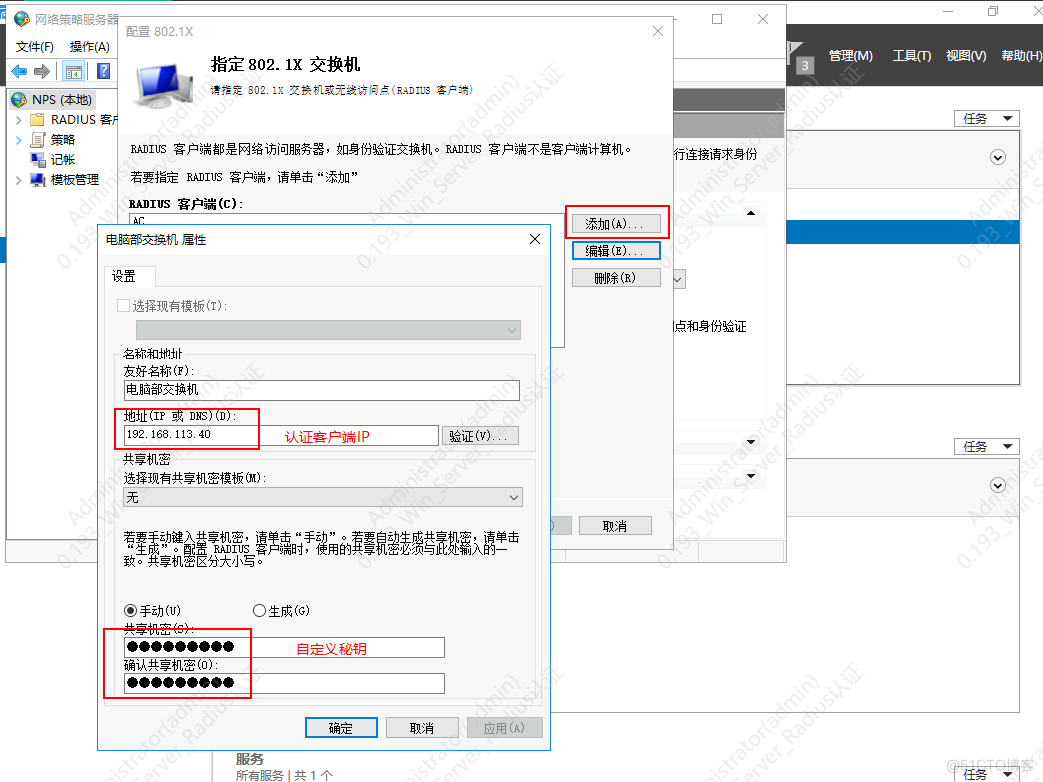
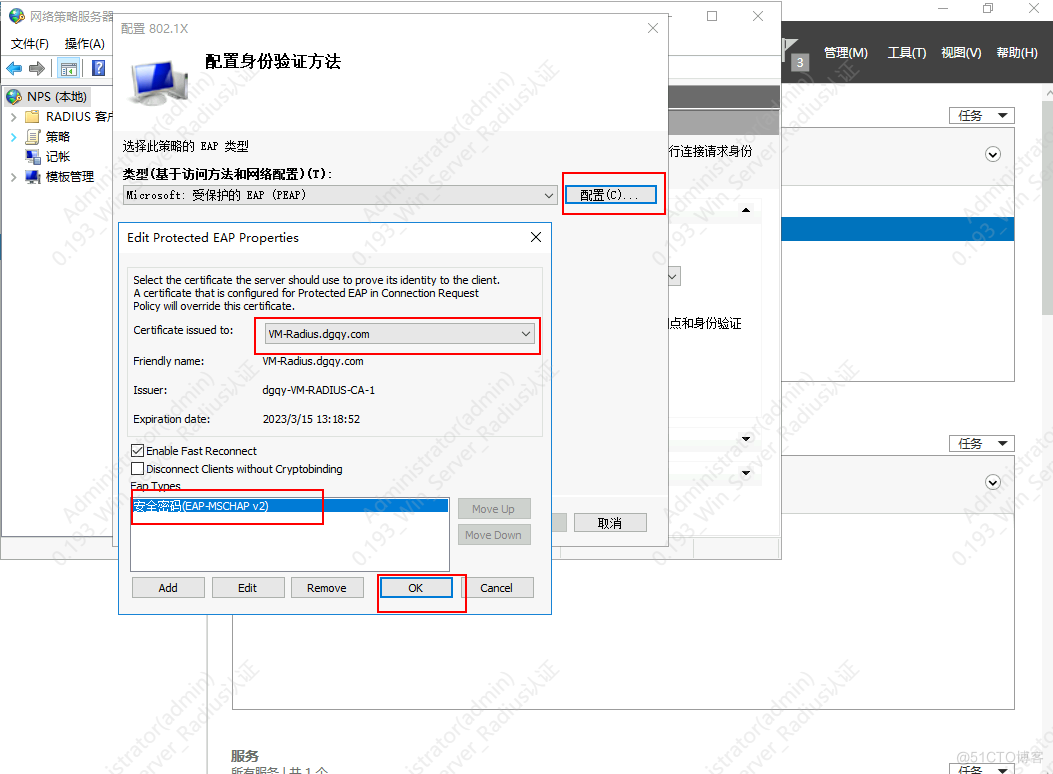
3.配置证书
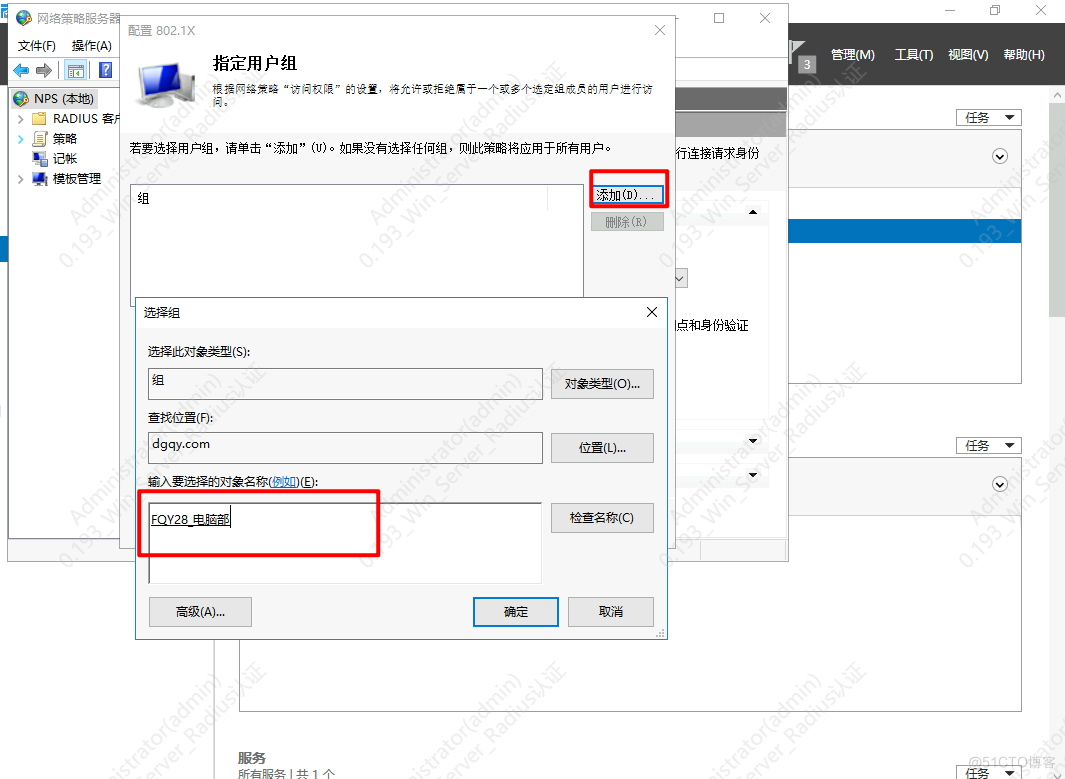
4.配置生效组
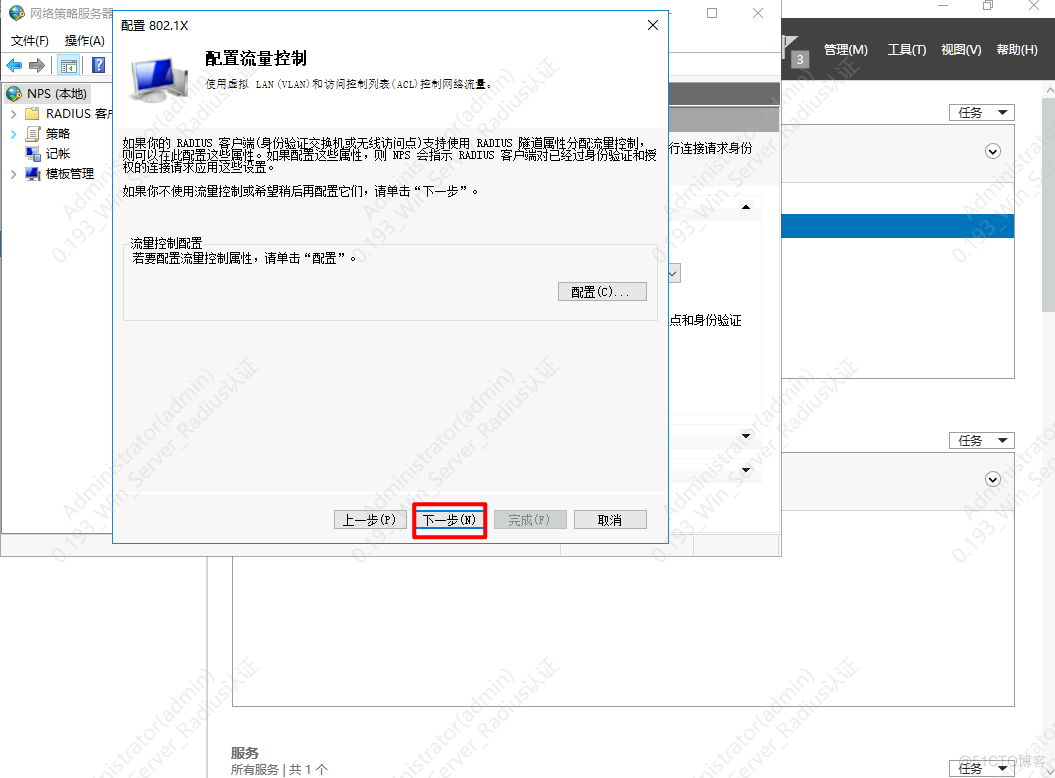
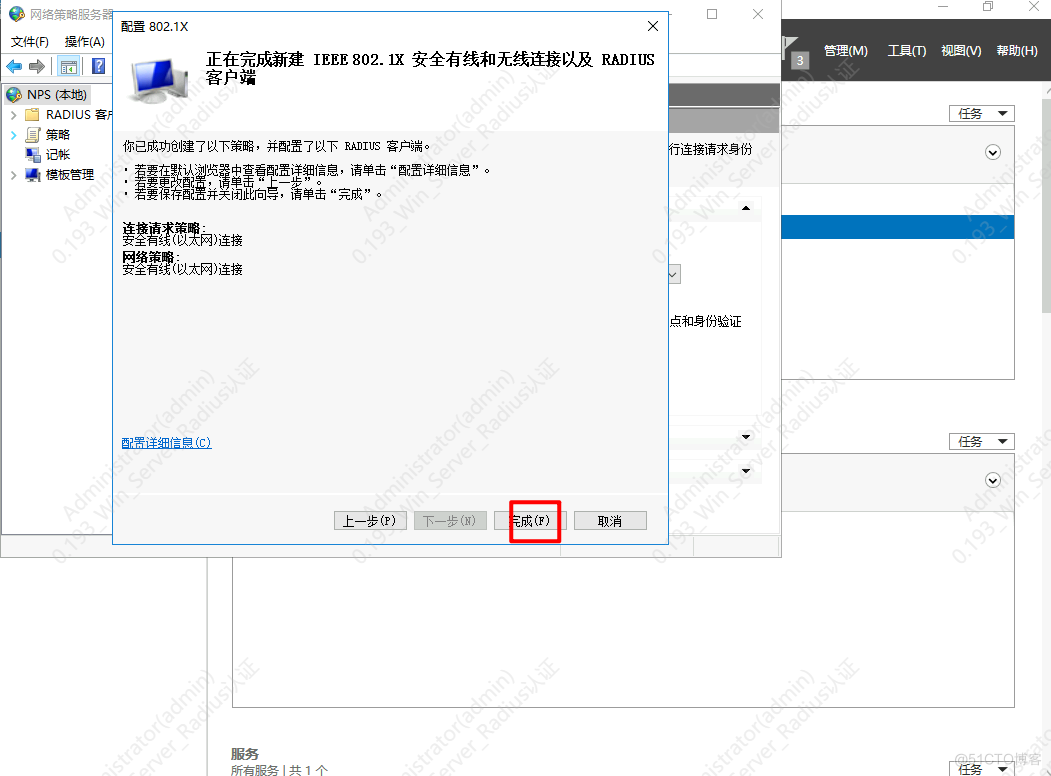
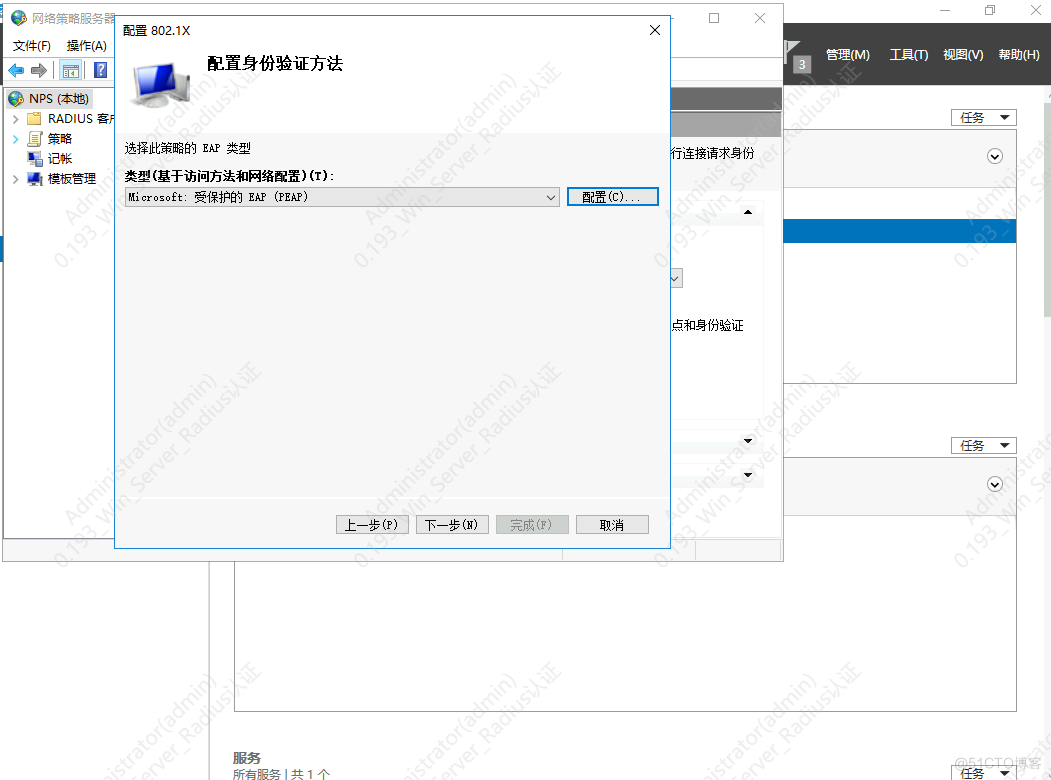
5.配置EAP认证类型
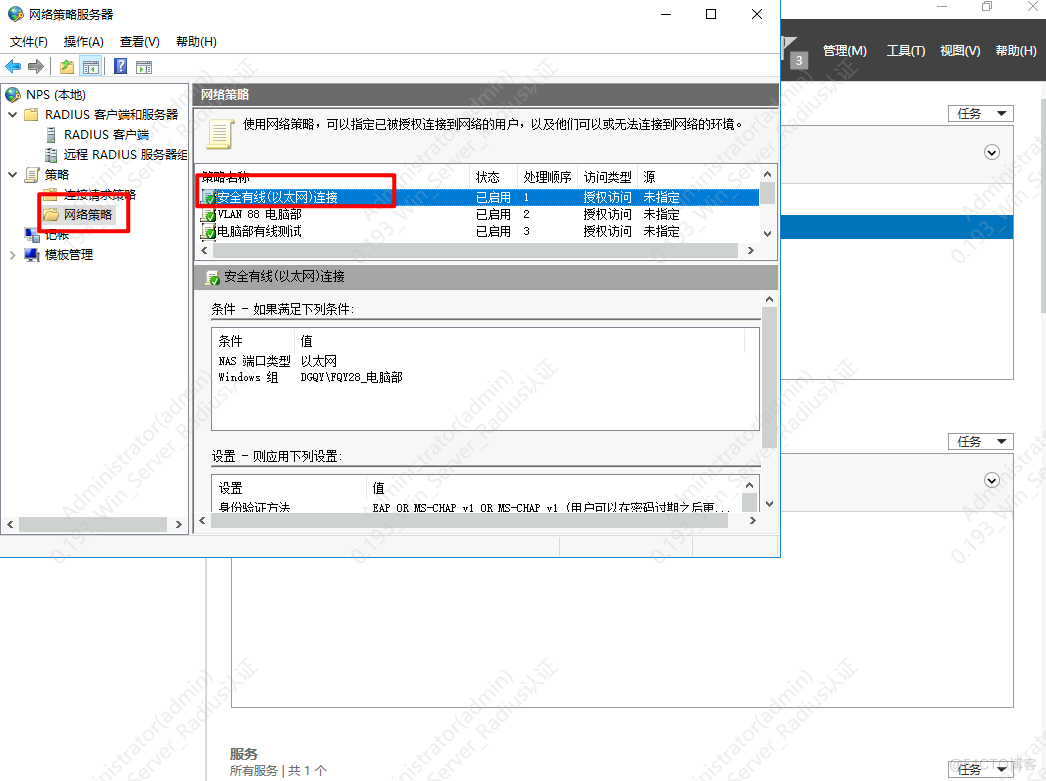
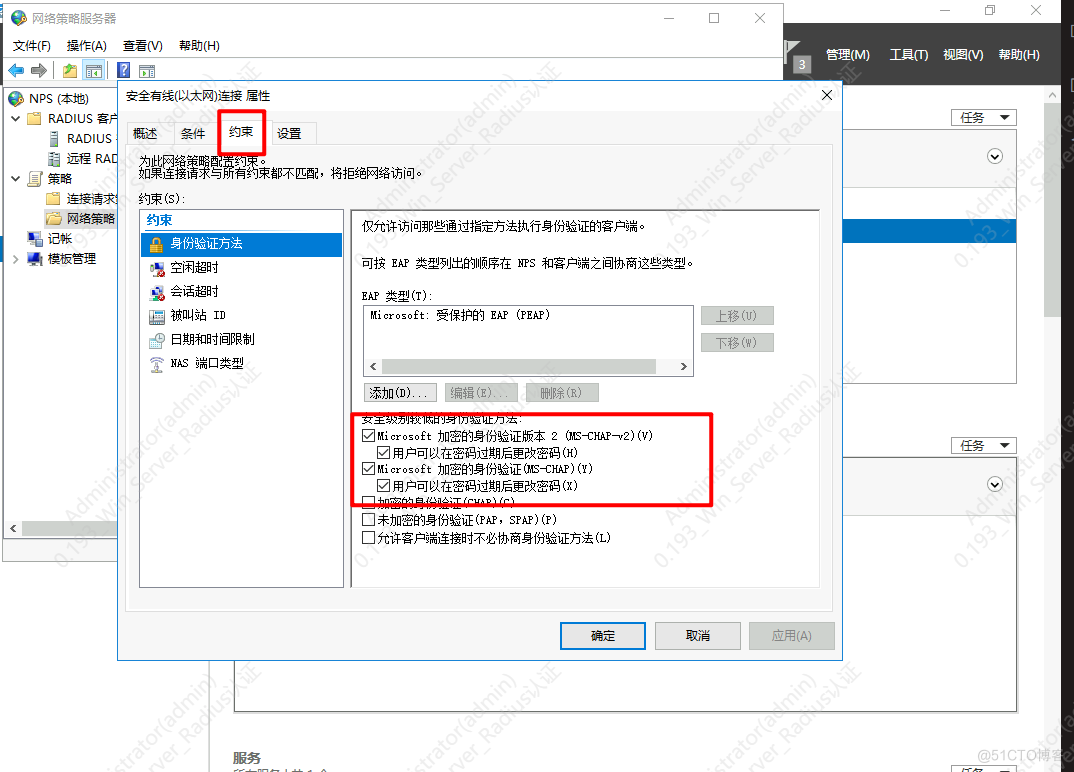
6.添加该组对应的vlan
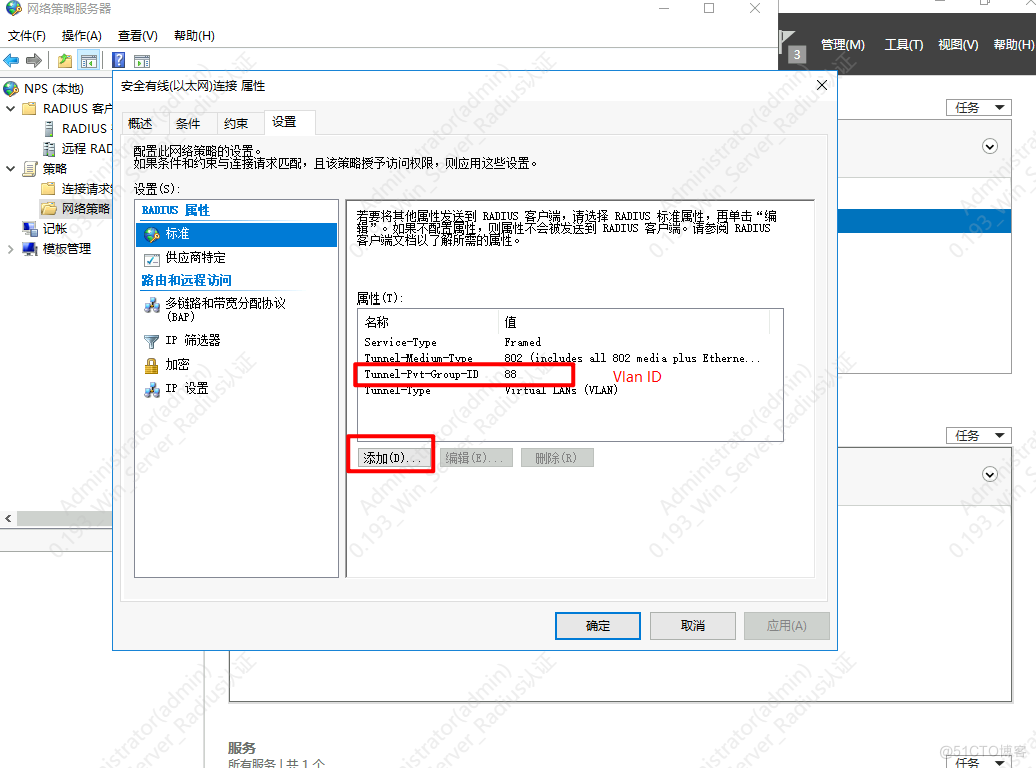
配置完成
四、客户端H3C交换机配置1.开启全局802.1x[QY_A_4F_IT_S5024_W1]dot1x[QY_A_4F_IT_S5024_W1]dot1x authentication-method eap2.配置Radius方案[QY_A_4F_IT_S5024_W1]radius scheme dgqy# 配置主认证/计费服务器IP[QY_A_4F_IT_S5024_W1-radius-dgqy]primary authentication 192.168.0.193[QY_A_4F_IT_S5024_W1-radius-dgqy]primary accounting 192.168.0.193#(可选)配置备认证/计费服务器IP[QY_A_4F_IT_S5024_W1-radius-dgqy]secondary authentication 192.168.0.194[QY_A_4F_IT_S5024_W1-radius-dgqy]secondary accounting 192.168.0.194# 配置认证/计费秘钥[QY_A_4F_IT_S5024_W1-radius-dgqy] key authentication simple XXXX[QY_A_4F_IT_S5024_W1-radius-dgqy] key accounting simple XXXX# 配置给Raiuds服务器发送不带域名[QY_A_4F_IT_S5024_W1-radius-dgqy]user-name-format without-domain[QY_A_4F_IT_S5024_W1-radius-dgqy]quit3.配置ISP域[QY_A_4F_IT_S5024_W1]domain dgqy[QY_A_4F_IT_S5024_W1-isp-dgqy]authentication lan-access radius-scheme dgqy[QY_A_4F_IT_S5024_W1-isp-dgqy]authorization lan-access radius-scheme dgqy#由于没有采用计费,故设置为none[QY_A_4F_IT_S5024_W1-isp-dgqy]accounting lan-access none[QY_A_4F_IT_S5024_W1-isp-dgqy]quit4.端口802.1x配置#开启端口dot1x[QY_A_4F_IT_S5024_W1]int GigabitEthernet 1/0/13[QY_A_4F_IT_S5024_W1-GigabitEthernet1/0/13]dot1x#指定接入控制方式(默认采用MAC地址)[QY_A_4F_IT_S5024_W1-GigabitEthernet1/0/13]dot1x port-method macbased#指定认证域[QY_A_4F_IT_S5024_W1-GigabitEthernet1/0/13]dot1x mandatory-domain dgqy[QY_A_4F_IT_S5024_W1-GigabitEthernet1/0/13]quit以上就完成了端口的802.1x认证配置,但是由于采用了windows自带的802.1x认证,无法回应H3C的心跳报文,故要将心跳握手、组播告警关闭,如果采用H3C自带iNode客户端,可以忽略
[QY_A_4F_IT_S5024_W1-GigabitEthernet1/0/13]undo dot1x handshake[QY_A_4F_IT_S5024_W1-GigabitEthernet1/0/13]undo dot1x multicast-trigger[QY_A_4F_IT_S5024_W1-GigabitEthernet1/0/13]dot1x unicast-trigger端口默认配置
interface GigabitEthernet1/0/13 port access vlan 11 stp edged-port #按照实际需求进行配置,建议采用hybrid接口5.客户端验证1.开启802.1x认证
启动服务,找到Wired AutoConfig
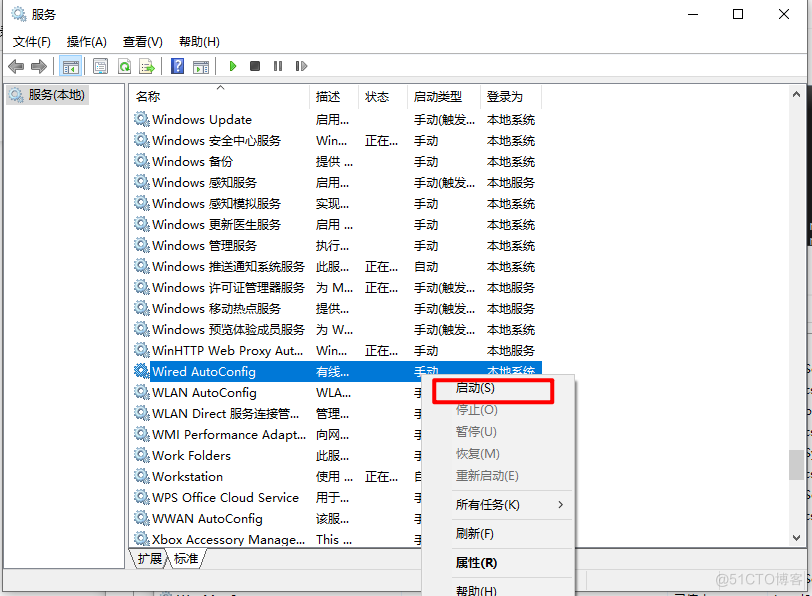

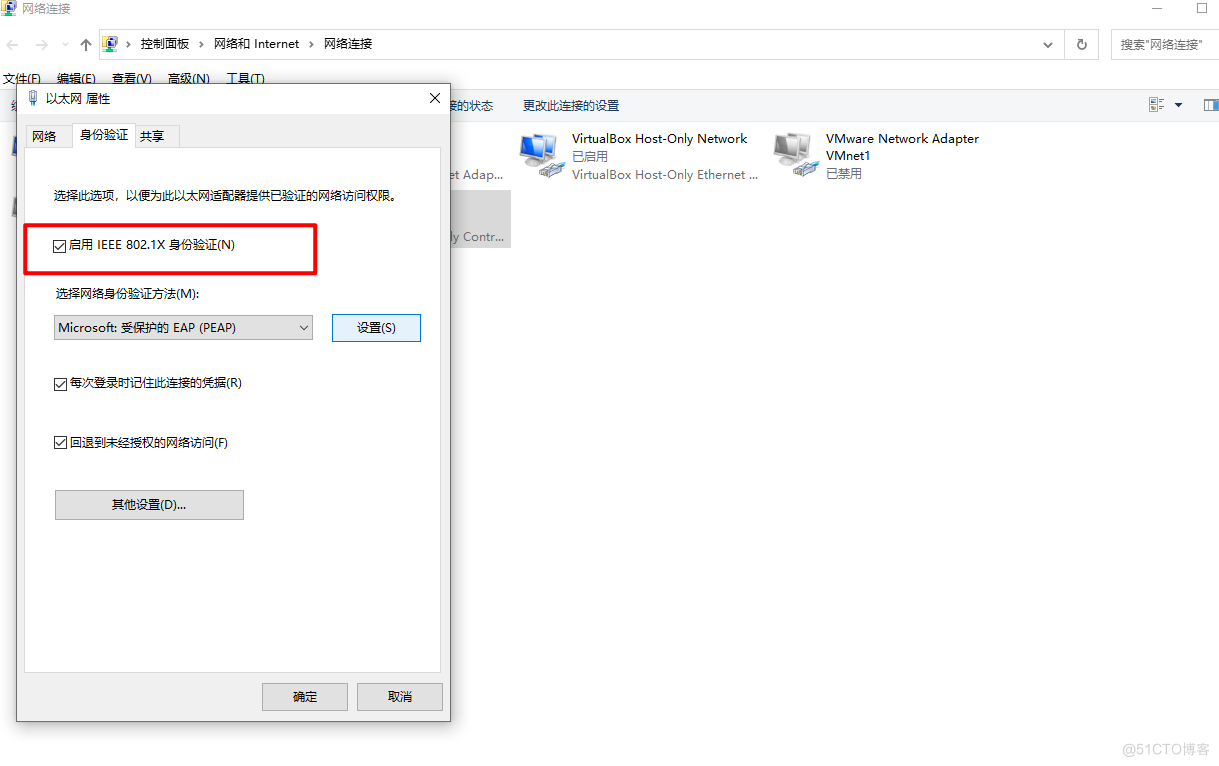
2.查看交换机动态vlan是否生效
[QY_A_4F_IT_S5024_W1]display interface brief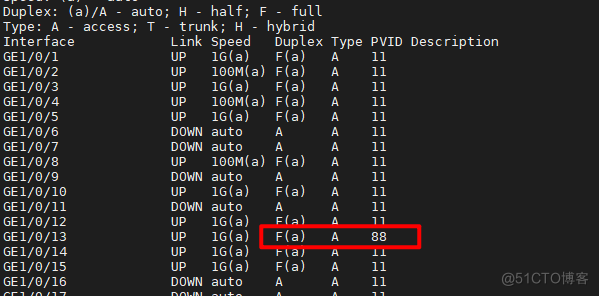
可以看得vlan自动更改为NPS中设置的vlan
五、配置802.1x无线认证连接AP的交换机配置如下
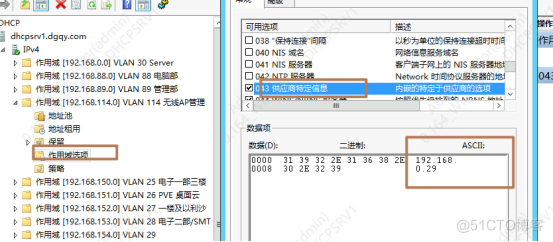
interface GigabitEthernet1/0/22 description WLAN-AP-TEST port link-type trunk port trunk permit vlan all port trunk pvid vlan 114# 默认AP获取到114网段的管理IP,通过放行对应vlan即可1.AC自动发现AP,需要在DHCP上配置option43
2.AC配置
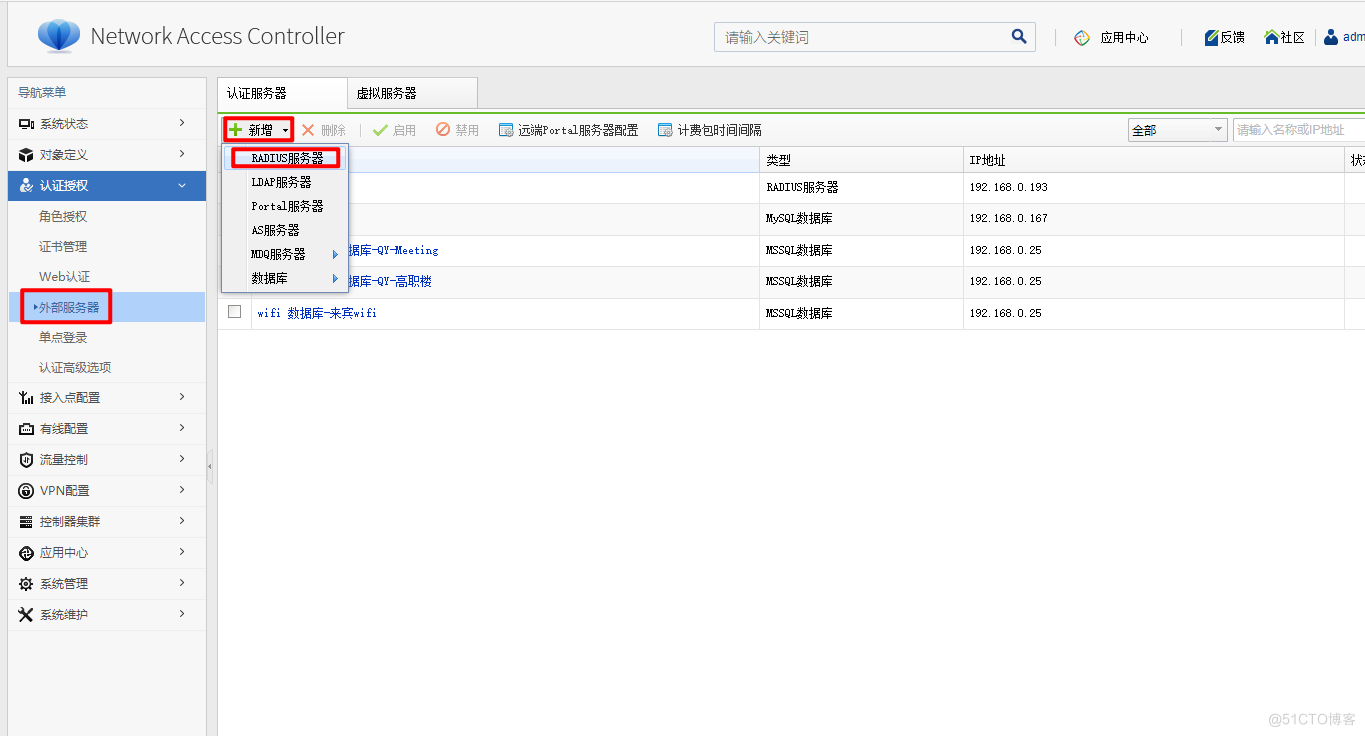
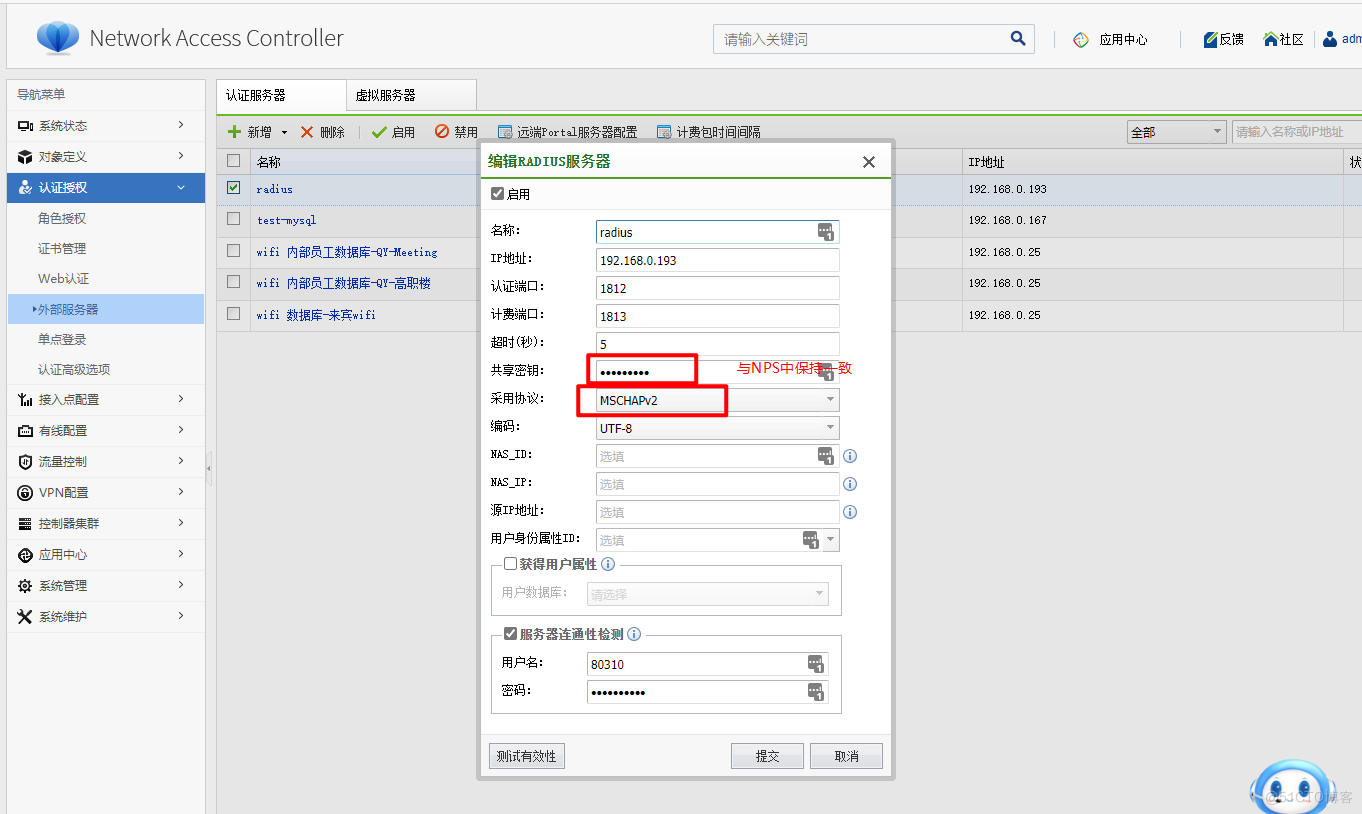
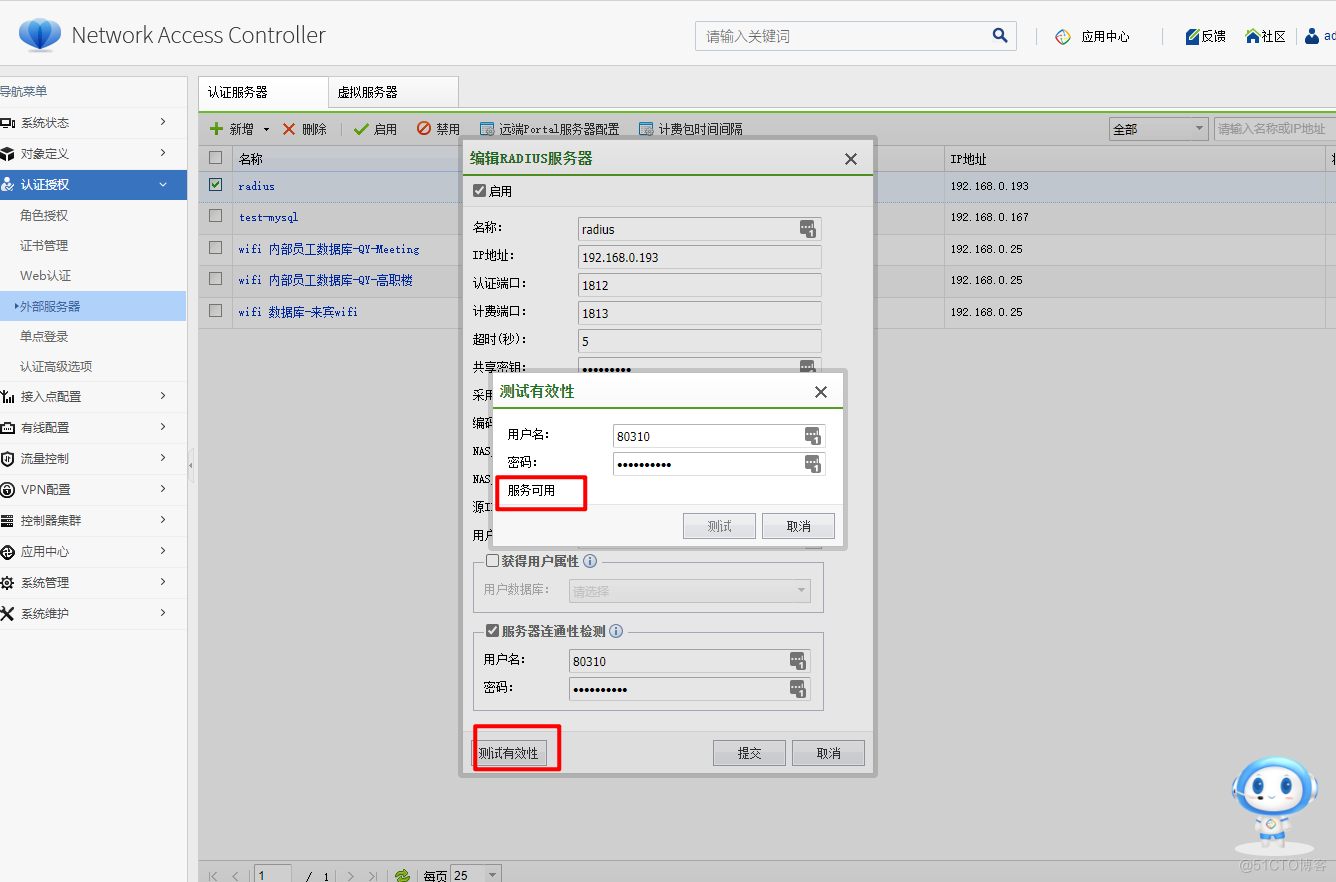
3.新增Raidus服务器
4.测试有效性
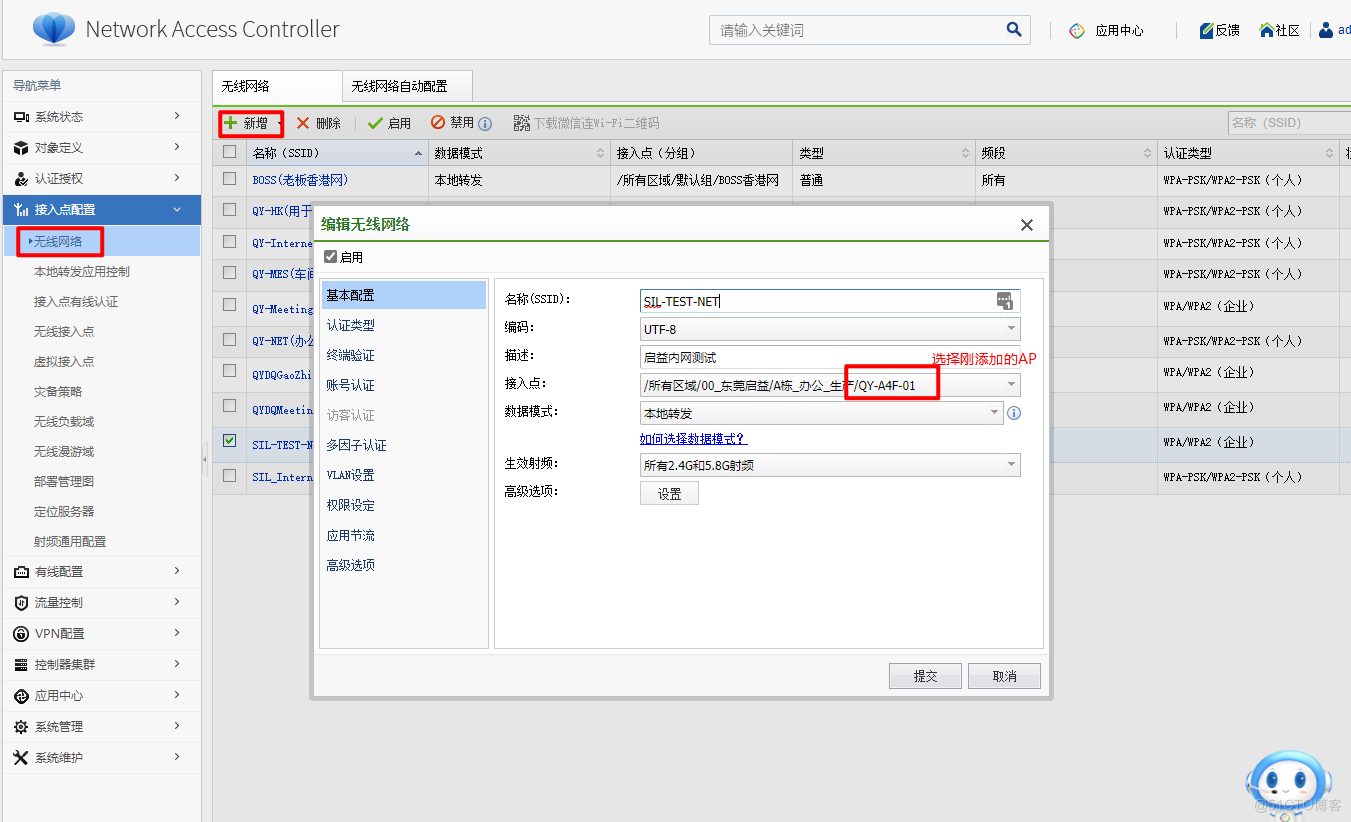
新增SSID
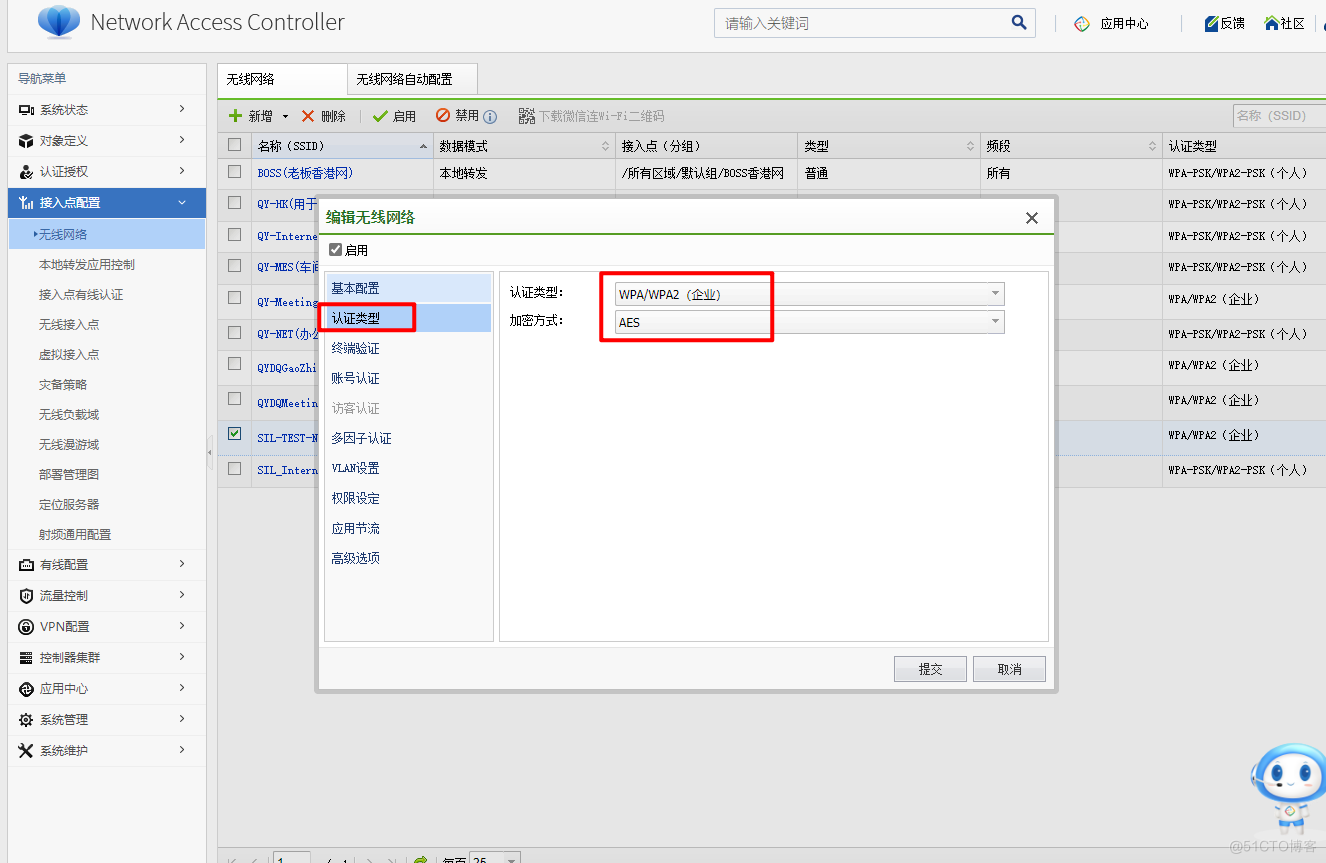
5.设置认证类型
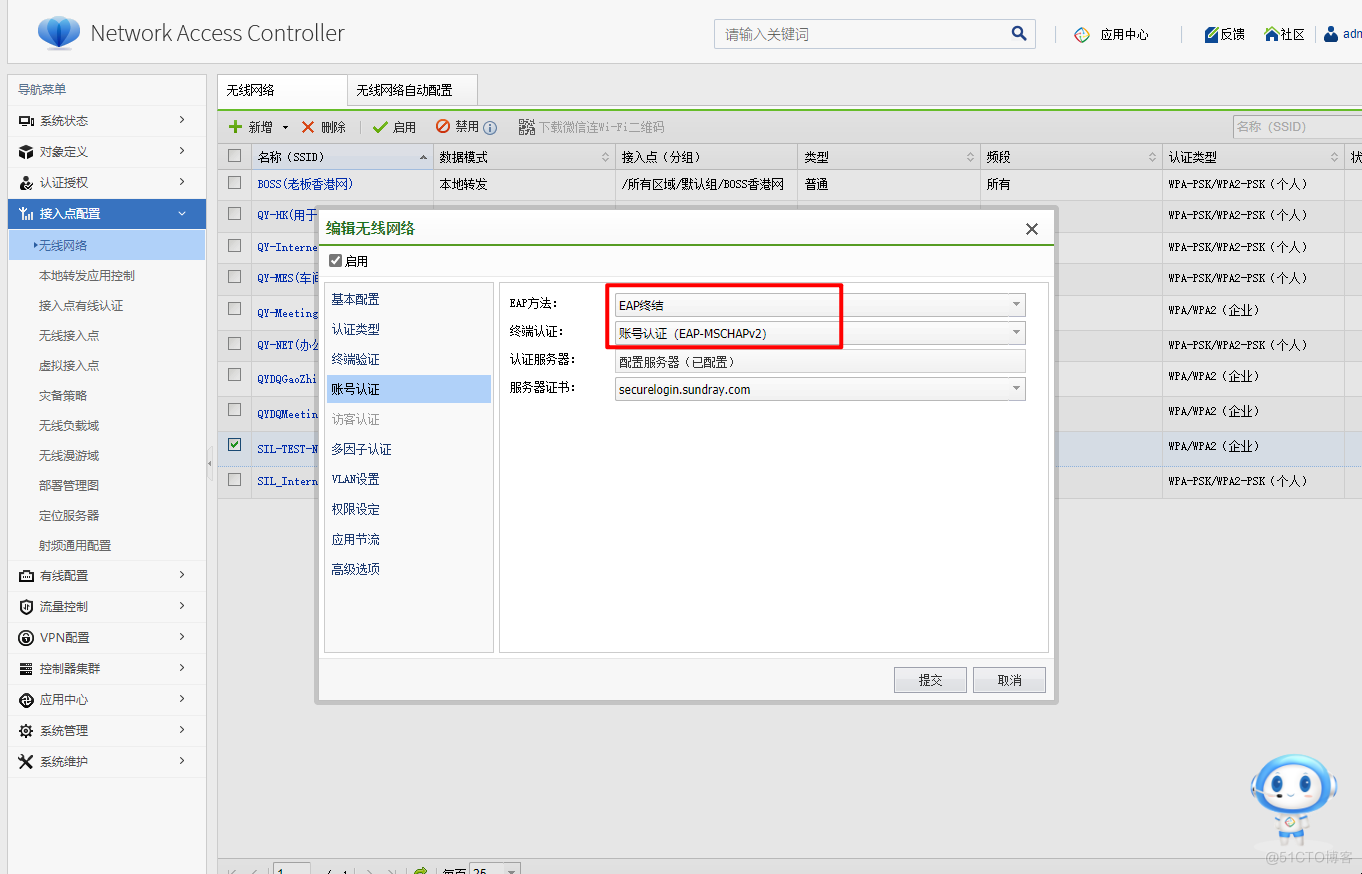
6.认证服务器配置

7.VLAN设置
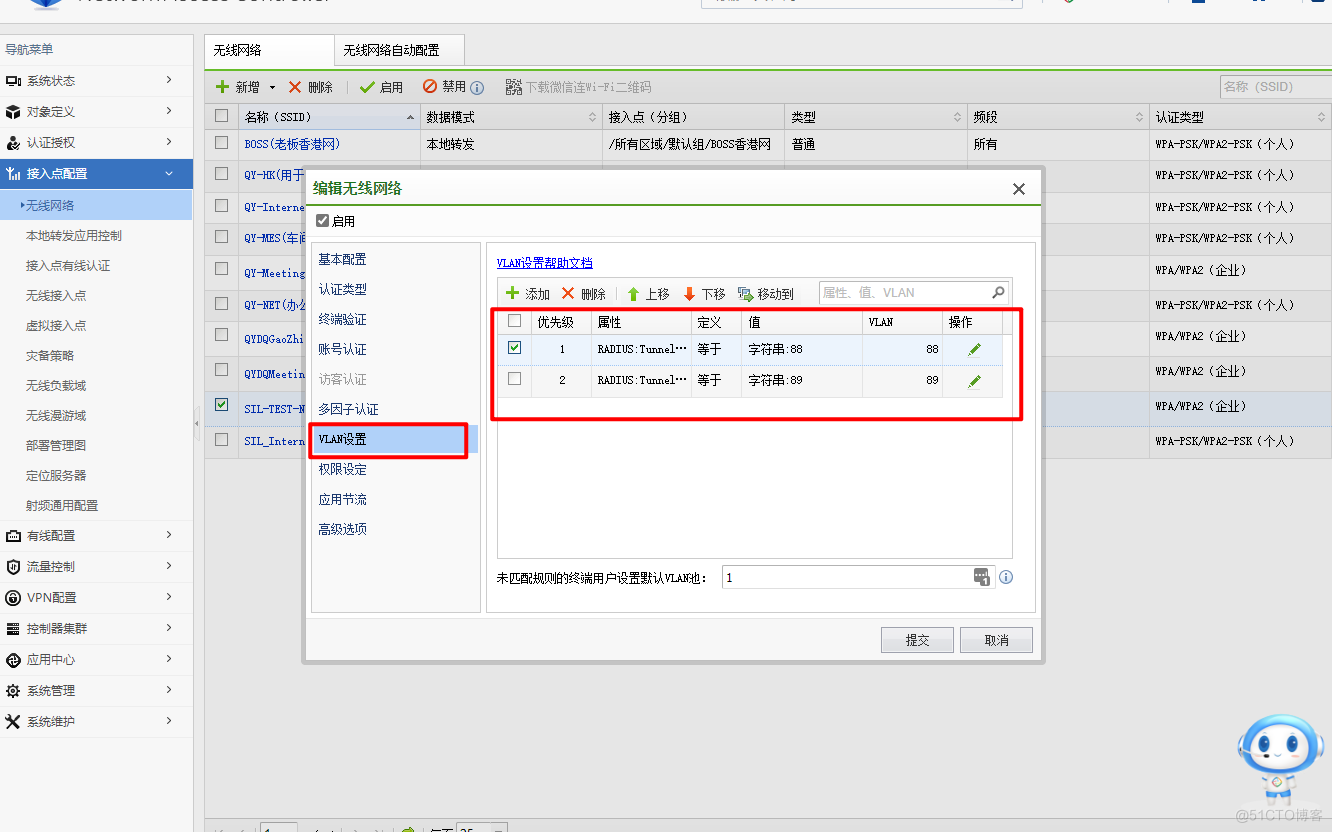
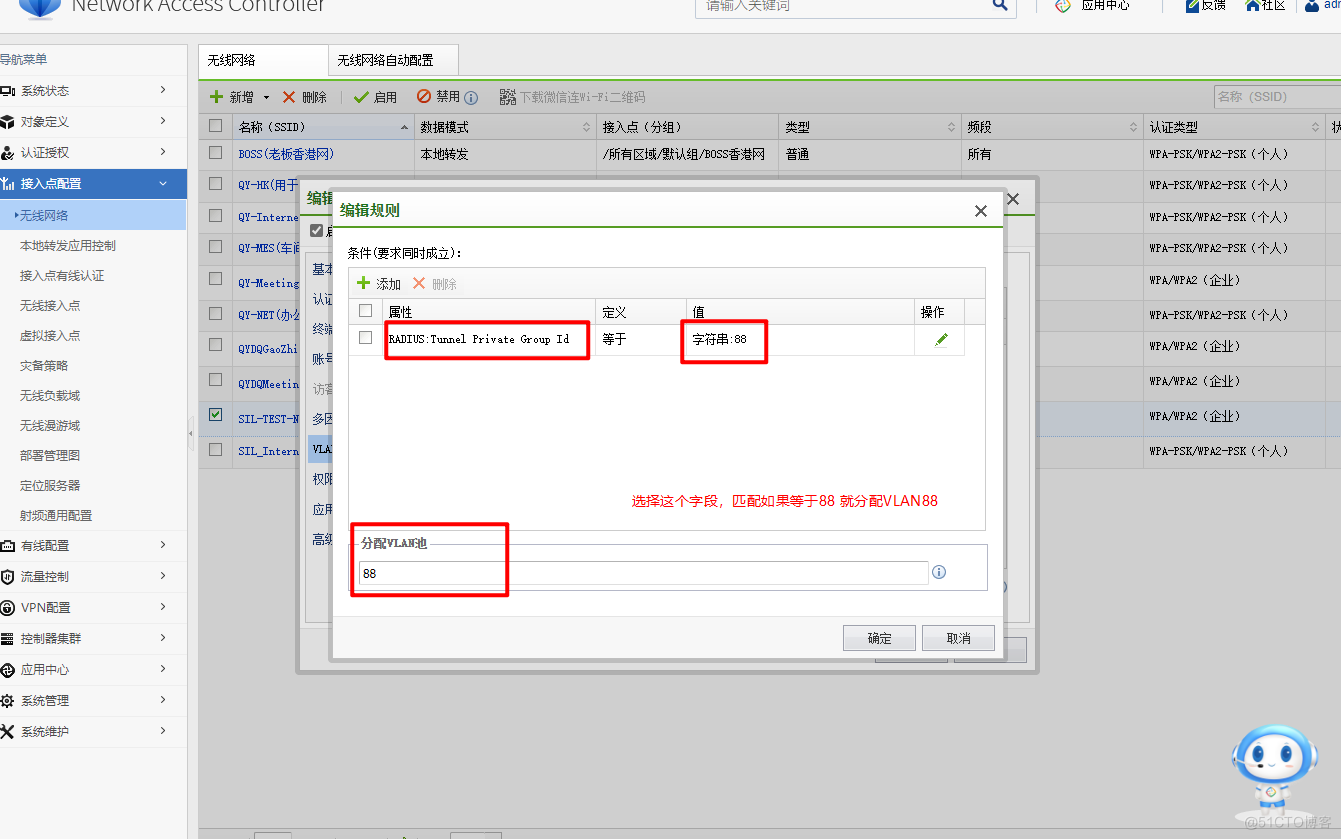
8.点击提交,使用无线连接,查看获取网段

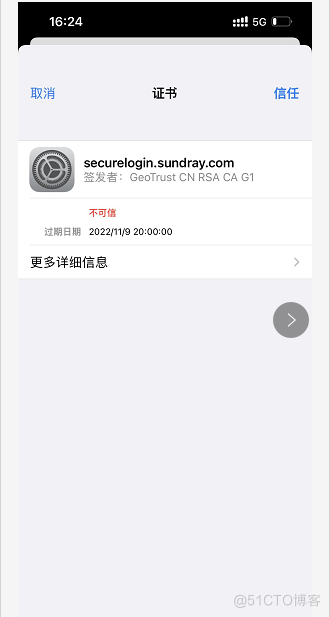
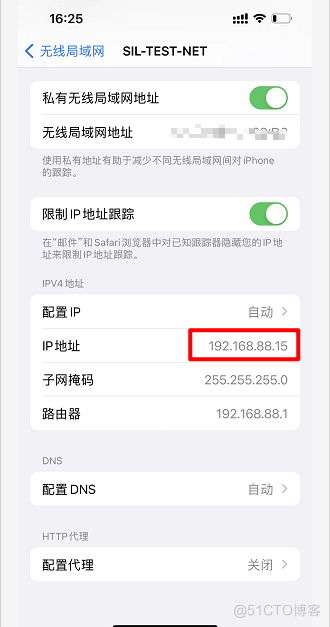
无线获取完成
六、故障排查思路如果无法正常获取网段,排查思路
1.NPS服务器认证日志
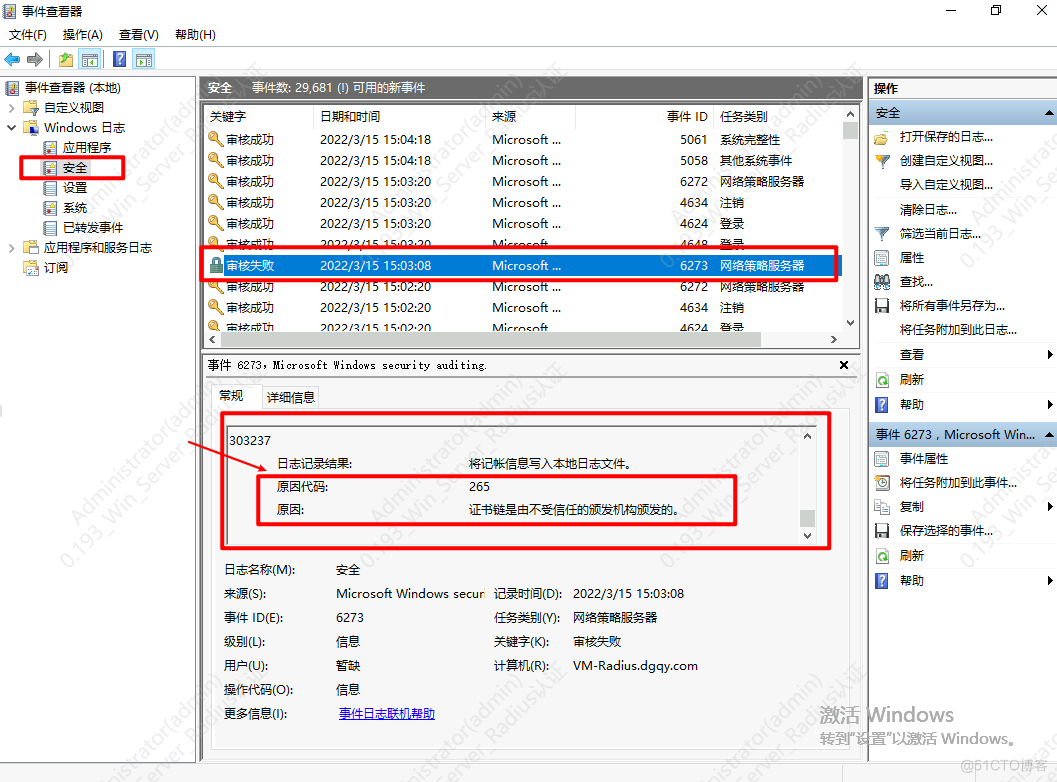
可以看得报错原因,常见的原因有 账号密码错误、EAP协议不支持、NPS端口类型配置错误、AD证书错误等
2.交换机故障排查
查看dot1x认证状态
# 查看接口的配置情况[QY_A_4F_IT_S5024_W1]display dot1x interface GigabitEthernet 1/0/13# 查看dot1x连接情况[QY_A_4F_IT_S5024_W1]display dot1x connection交换机debugging调试
debugging radius alldebugging dot1x allt mt d查看debugging日志,能查看报文具体到哪一个地方
EAP中继认证过程(该图转载至H3C配置手册)

查看报文
发送request packet
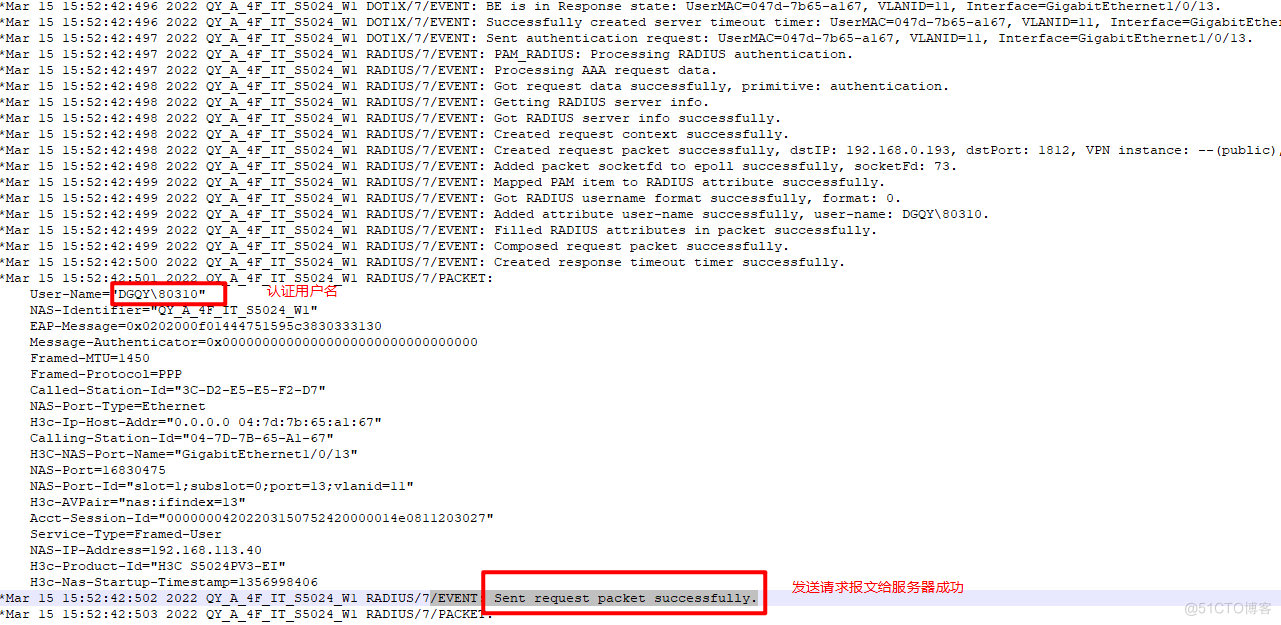
收到reply packet

通过对比报文就可以查到在哪个环节出了问题
综上
以上对windwos server 完成802.1x认证+动态vlan大致思路进行了整理,不仅用到了AD域控、DHCP、Radius服务器,还需要对H3C等品牌交换机的配置进行掌握,同时采用了无线信锐AC+AP的形式完成网络认证场景全覆盖,后续将介绍在此场景中,访客网络的接入与认证失败网络接入场景。