A zero-day (0day) exploit is a cyber attack targeting a software vulnerability which is unknown to the software vendor or to antivirus vendors. The attacker spots the software vulnerability before any parties interested in mitigating it, quickly creates an exploit, and uses it for an attack. Such attacks are highly likely to succeed because defenses are not in place. This makes zero-day attacks a severe security threat.
Typical attack vectors include Web browsers, which are common targets due to their ubiquity, and email attachments that exploit vulnerabilities in the application opening the attachment, or in specific file types such as Word, Excel, PDF or Flash.
A related concept is zero-day malware — a computer virus for which specific antivirus software signatures are not yet available, so signature-based antivirus software cannot stop it.
Typical targets for a zero-day exploit include:
Government departments.Large enterprises.Individuals with access to valuable business data, such as intellectual property.Large numbers of home users who use a vulnerable system, such as a browser or operating system. Hackers can use vulnerabilities to compromise computers and build massive botnets.Hardware devices, firmware and Internet of Things (IoT).In some cases governments use zero-day exploits to attack individuals, organizations or countries who threaten their natural security.Because zero-day vulnerabilities are valuable for different parties, a market exists in which organizations pay researchers who discover vulnerabilities. In addition to this ‘white market’, there are gray and black markets in which zero-day vulnerabilities are traded, without public disclosure, for up to hundreds of thousands of dollars.
Examples of zero-day attacksSome high-profile examples of zero-day attacks include:
Stuxnet: This malicious computer worm targeted computers used for manufacturing purposes in several countries, including Iran, India, and Indonesia. The primary target was Iran’s uranium enrichment plants, with the intention of disrupting the country’s nuclear program.The zero-day vulnerabilities existed in software running on industrial computers known as programmable logic controllers (PLCs), which ran on Microsoft Windows. The worm infected the PLCs through vulnerabilities in Siemens Step7 software, causing the PLCs to carry out unexpected commands on assembly line machinery, sabotaging the centrifuges used to separate nuclear material.Sony zero-day attack: Sony Pictures was the victim of a zero-day exploit in late 2014. The attack crippled Sony’s network and led to the release of sensitive corporate data on file-sharing sites. The compromised data included details of forthcoming movies, business plans, and the personal email addresses of senior Sony executives. The details of the exact vulnerability exploited in the Sony attack remains unknown.RSA: In 2011, hackers used a then-unpatched vulnerability in Adobe Flash Player to gain access to the network of security company RSA. The attackers sent emails with Excel spreadsheet attachments to small groups of RSA employees. The spreadsheets contained an embedded Flash file that exploited the zero-day Flash vulnerability. When one of the employees opened the spreadsheet, the attacked installed the Poison Ivy remote administration tool to take control of the computer.Once they gained access to the network, attackers searched for sensitive information, copied it and transmitted it to external servers they controlled. RSA admitted that among the data stolen was sensitive information related to the company’s SecurID two-factor authentication products, used around the world for access to sensitive data and devices.Operation Aurora: This 2009 zero-day exploit targeted the intellectual property of several major enterprises, including Google, Adobe Systems, Yahoo, and Dow Chemical. The vulnerabilities existed in both Internet Explorer and Perforce; the latter was used by Google to manage its source code. Nov 7 Upcoming WebinarElevate your Security Posture by Balancing Effectiveness and Efficiency
Nov 7 Upcoming WebinarElevate your Security Posture by Balancing Effectiveness and EfficiencyRegister Now
Zero-day vulnerability detectionBy definition, no patches or antivirus signatures exist yet for zero-day exploits, making them difficult to detect. However, there are several ways to detect previously unknown software vulnerabilities.
Vulnerability scanningVulnerability scanning can detect some zero-day exploits. Security vendors who offer vulnerability scanning solutions can simulate attacks on software code, conduct code reviews, and attempt to find new vulnerabilities that may have been introduced after a software update.
This approach cannot detect all zero-day exploits. But even for those it detects, scanning is not enough—organizations must act on the results of a scan, perform code review and sanitize their code to prevent the exploit. In reality most organizations are slow to respond to newly discovered vulnerabilities, while attackers can be very quick to exploit a zero-day exploit.
Patch managementAnother strategy is to deploy software patches as soon as possible for newly discovered software vulnerabilities. While this cannot prevent zero-day attacks, quickly applying patches and software upgrades can significantly reduce the risk of an attack.
However, there are three factors that can delay the deployment of security patches. Software vendors take time to discover vulnerabilities, develop a patch and distribute it to users. It can also take time for the patch to be applied on organizational systems. The longer this process takes, the higher the risk of a zero-day attack.
Input validation and sanitizationInput validation solves many of the issues inherent in vulnerability scanning and patch management. It doesn’t leave organizations unprotected while they are patching systems or sanitizing code—processes that can take time. It is operated by security experts and is much more flexible, able to adapt and respond to new threats in real time.
One of the most effective ways to prevent zero-day attacks is deploying a web application firewall (WAF) on the network edge. A WAF reviews all incoming traffic and filters out malicious inputs that might target security vulnerabilities.
Additionally, the most recent advancement in the fight against zero-day attacks is runtime application self-protection (RASP). RASP agents sit inside applications, examining request payloads with the context of the application code at runtime, to determine whether a request is normal or malicious- enabling applications to defend themselves.
Zero-day initiativeA program established to reward security researchers for responsibly disclosing vulnerabilities, instead of selling the information on the black market. Its objective is to create a broad community of vulnerability researchers who can discover security vulnerabilities before hackers do, and alert software vendors.
See how Imperva Web Application Firewall can help you with zero-day exploits.
Request demoLearn moreImperva zero-day threat mitigationVulnerability scanning and patch management are partial solutions to zero-day attacks. And they create a large window of vulnerability, due to the time it takes to develop and apply patches and code fixes.
Imperva’s Web Application Firewall (WAF) is a managed input validation service deployed at the edge of your network which intelligently filters and verifies incoming traffic, blocking attacks at the network edge.
Imperva RASP is the latest innovation in the fight against zero-day attacks. Using patented grammar-based techniques that leverage LangSec, RASP allows applications to defend themselves without signatures or patches- providing security by default and sparing you the operational costs of off-cycle 0-day patching.
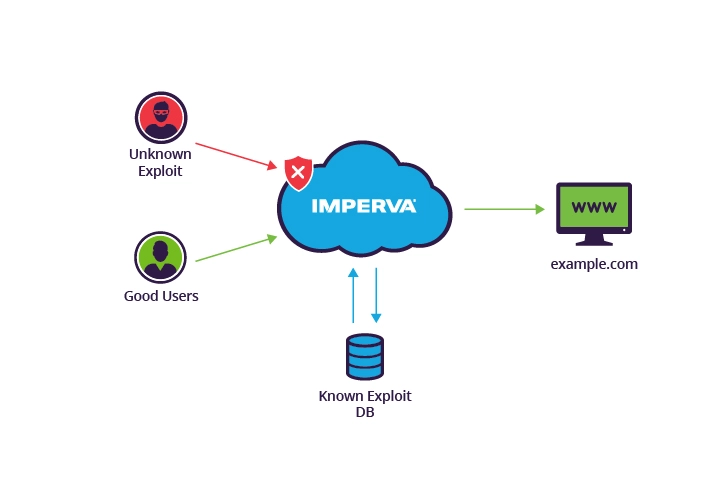
Imperva cloud-based WAF blocks zero-day attacks by using crowdsourced security to identify new threats
Imperva cloud-based WAF leverages crowdsourced security to protect against zero-day attacks, aggregating attack data to react to threats instantly. As soon as a new threat is identified anywhere on the Incapsula network, a mitigation path is quickly deployed to safeguard the entire user base.